BitWall CTF
From 2nd to 4th May, Bitwall/ Bitsiege CTF occurred in which I participated and tackled a few challenges. Let's dive in.
Since the server belonging to the website is not working, I'll have to give vague descriptions of the challenges.
Cryptography
Fr33 Fl4g
This was a great challenge since I was the first one to solve it. I'm sure that other competitors failed to solve it early on since they never met such encoding/encryption before.
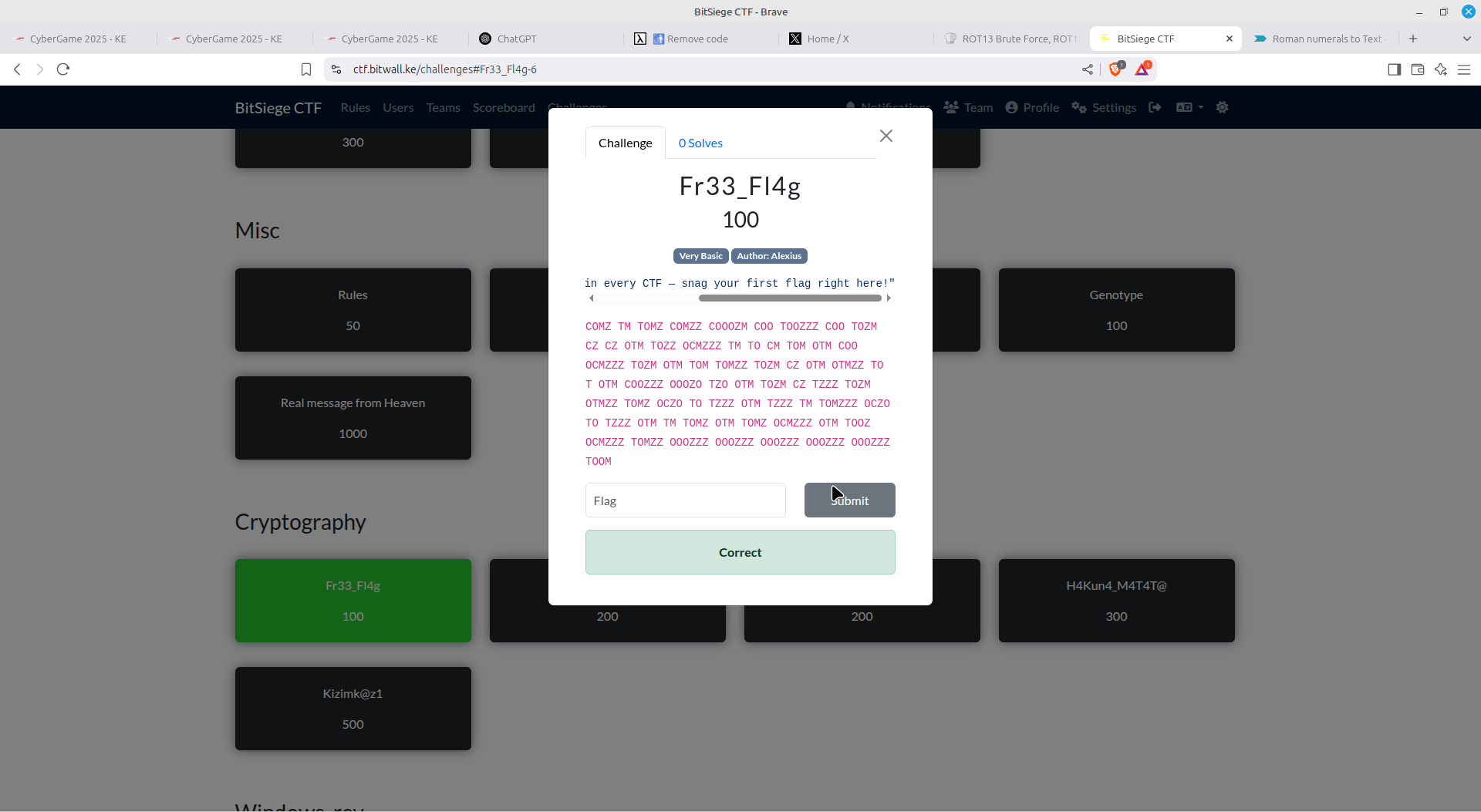
I too never did, but dealt with it on another CTF just a few days ago! Cybergame.
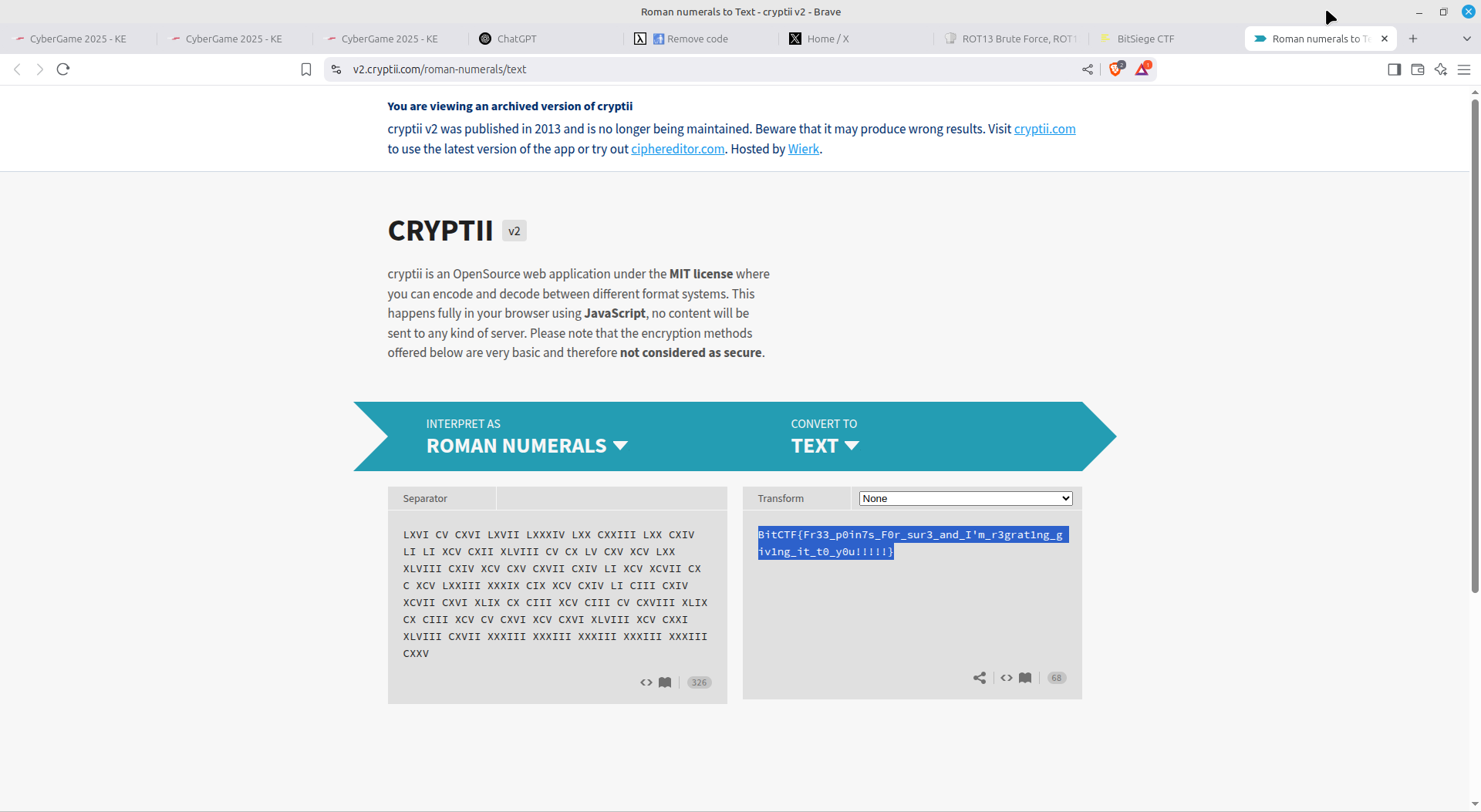
All one had to do is perform a ROT13 brute force on the text provided (ROT13 with 9 rotations provides Roman numerals), then convert the Roman Numerals to text. I used Cryptii.com

Forensics
Silent Supernova series
It involves downloading a malicious Microsoft word document and performing some forensics on it.
1
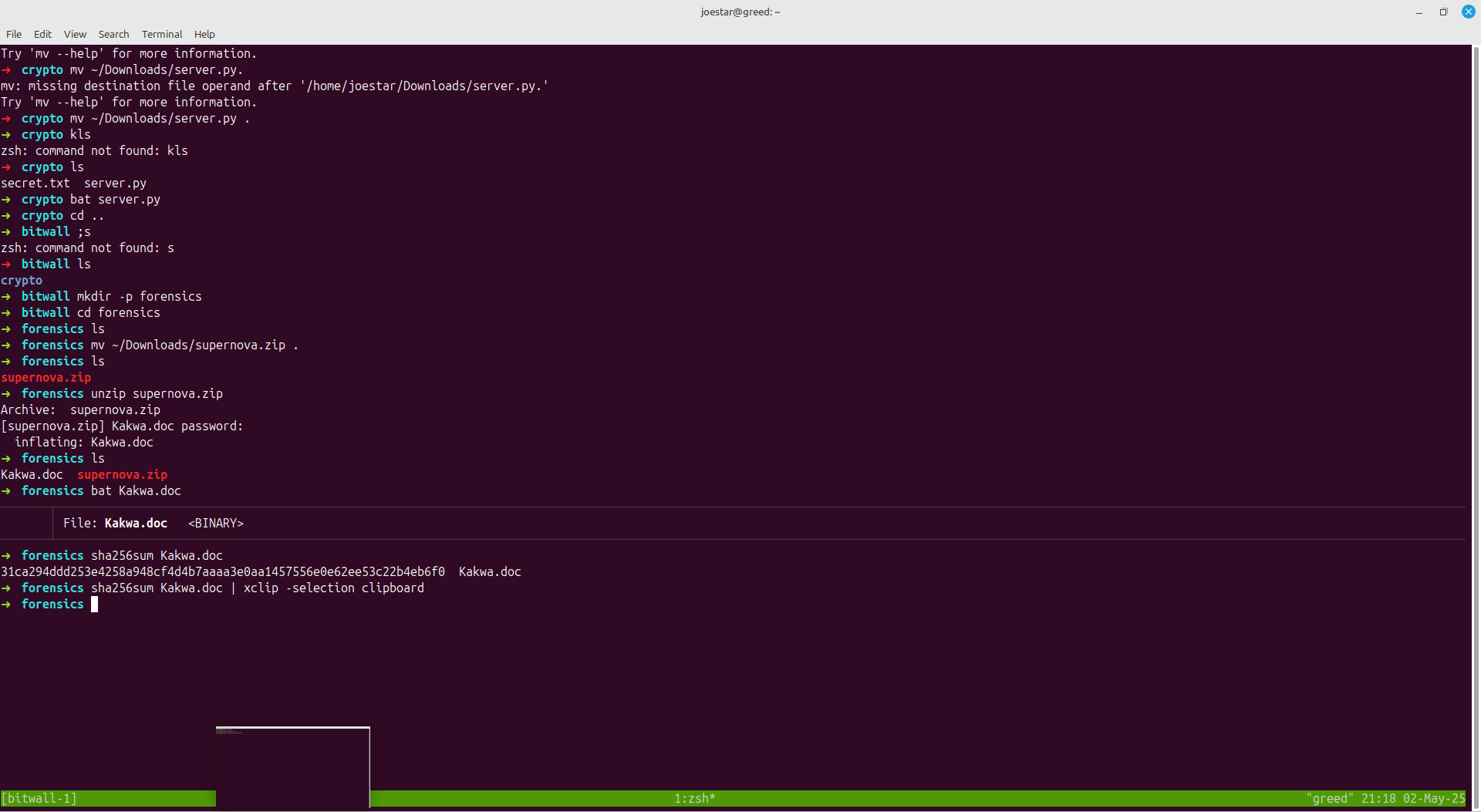
For the first level, all we had to do is to check the sha256sum hash of the file, as shown below.
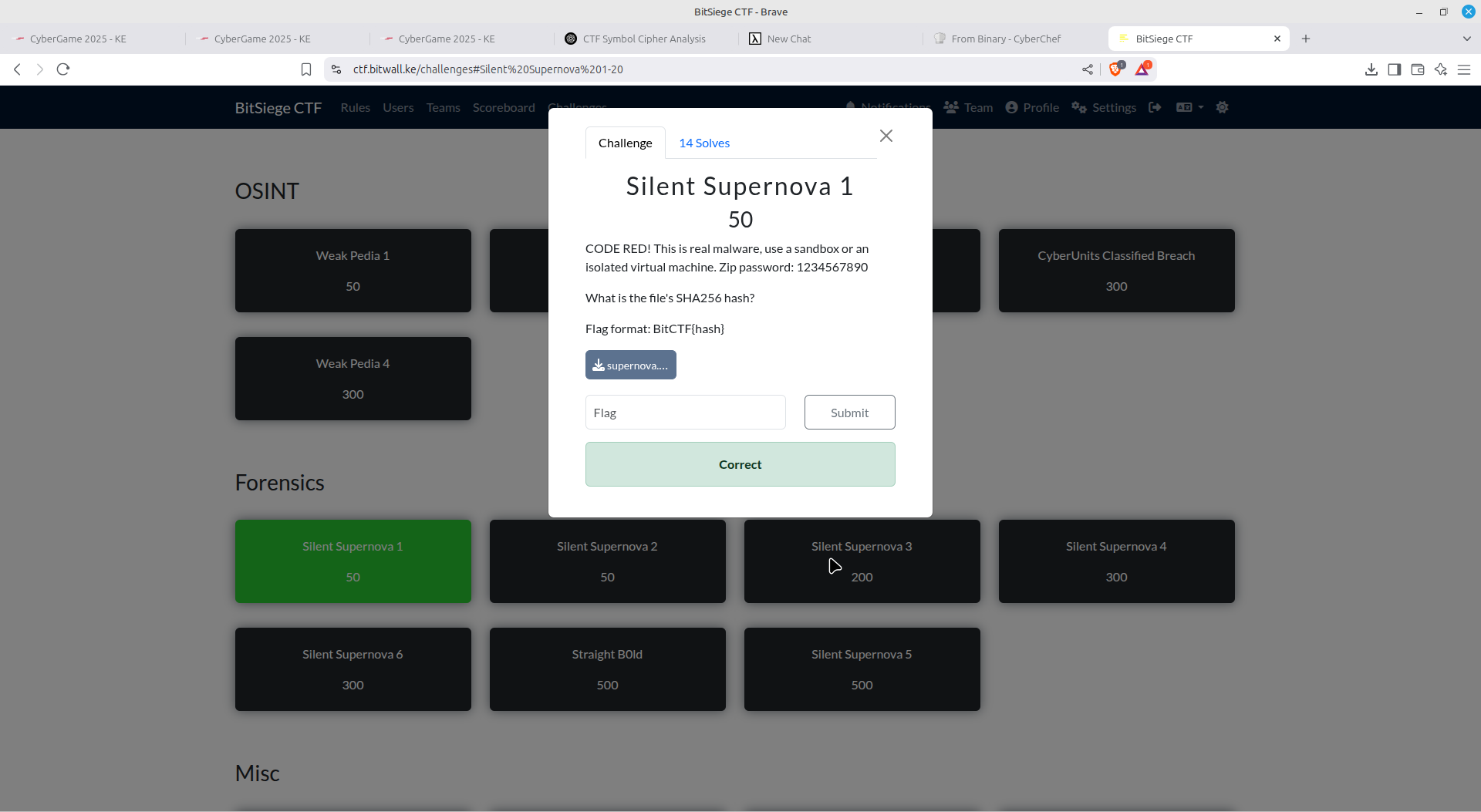
sha256sum Kakwa.doc
2
For the second level, it specifically asked for the file's size but in bytes
This can be done through:
stat -c %s Kakwa.doc

Random
Rules
The description was for one to head for the website's rules page and look for anything not normal.
On checking the source code for the page, we get to see some HTML comment on what appears to be base64 encoded writing
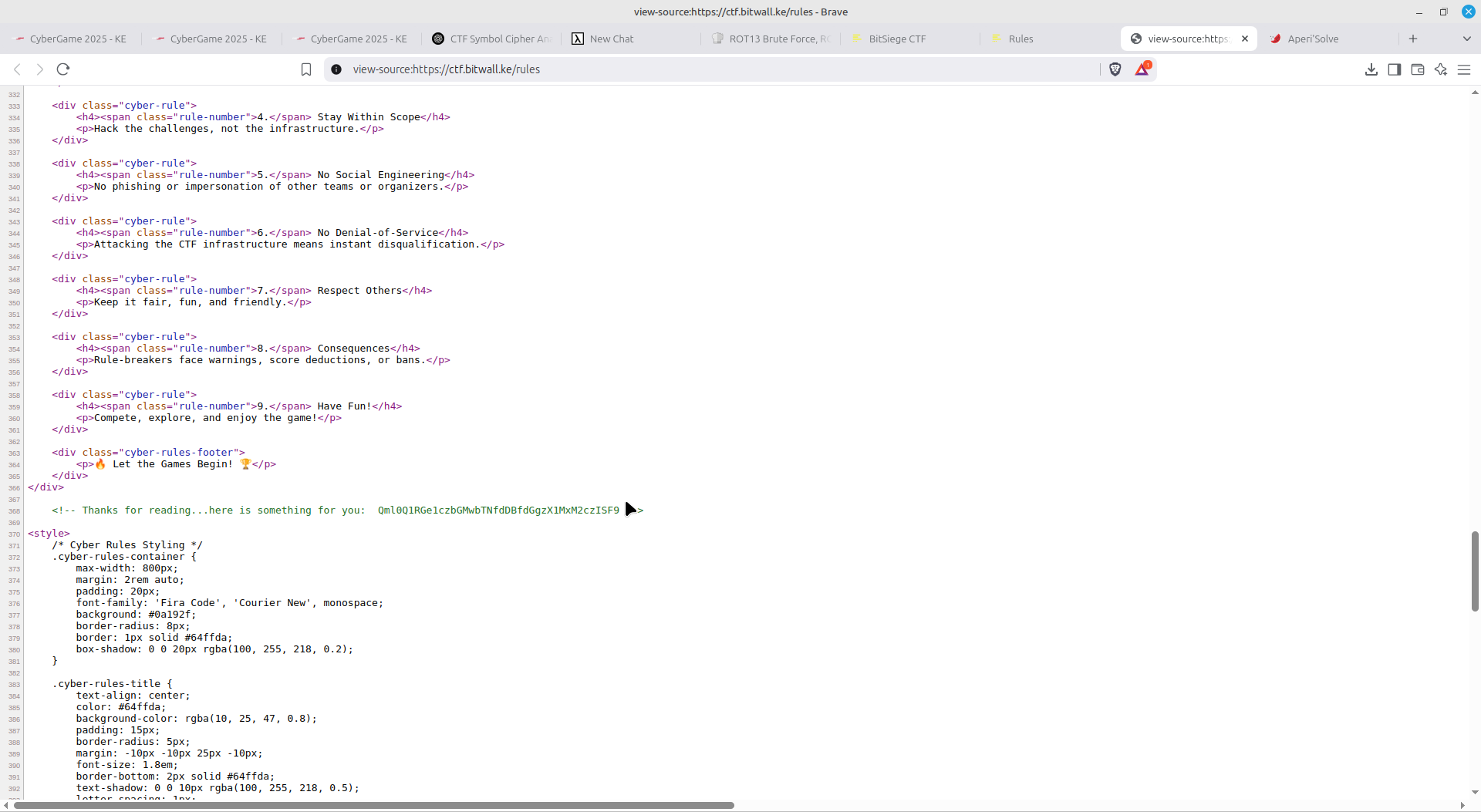
Headed onto Cyberchef, decoded and obtained the flag!
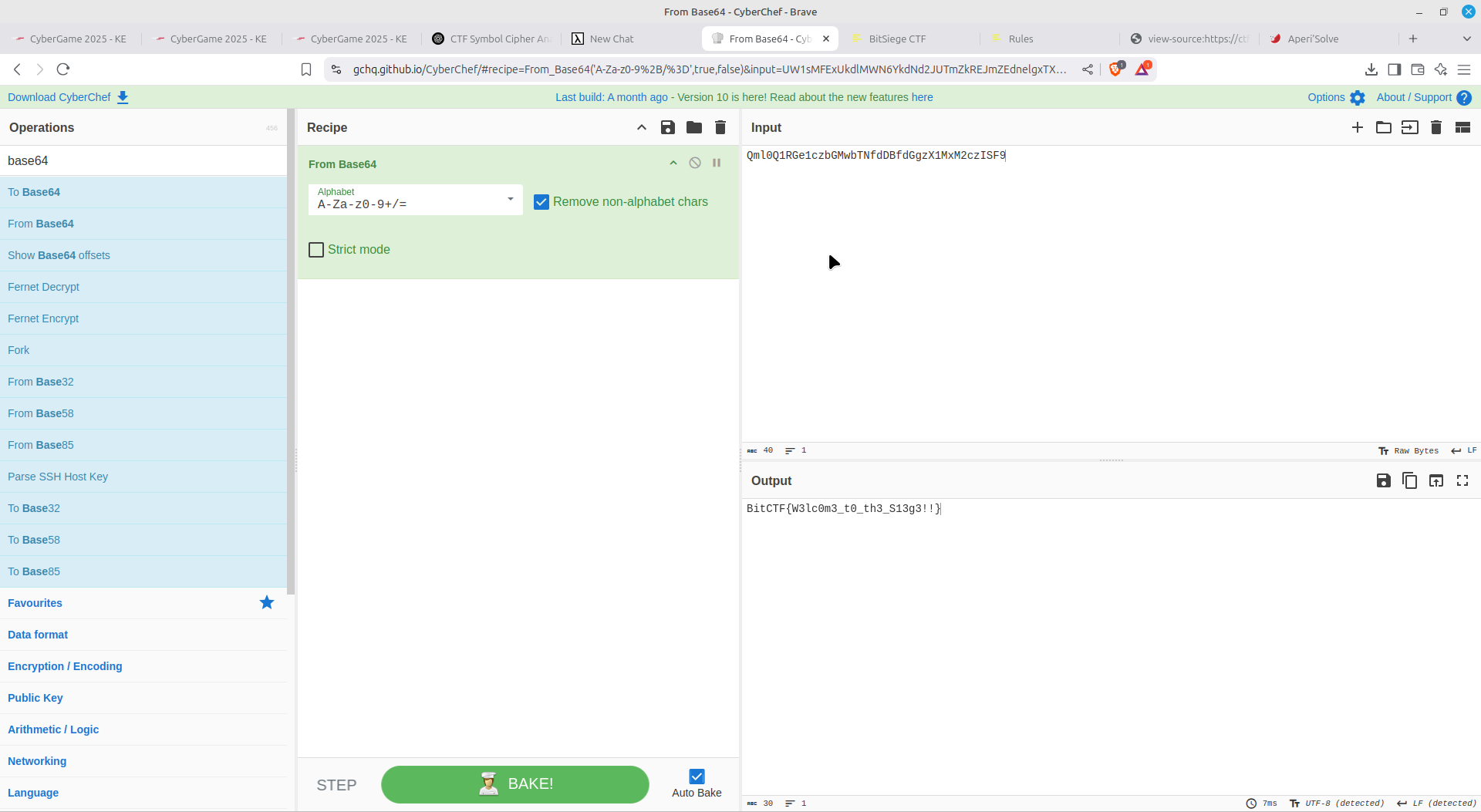
I could have solved even more challenges however I had limited time!
Thank you for reading!